Kaspersky GReAT (Global Research and Analysis Team) experts have discovered open-source packages that download the Quasar backdoor and a stealer designed to exfiltrate cryptocurrency. The malicious packages are intended for the Cursor development environment, which is based on Visual Studio Code — a tool used for AI-assisted coding.
The malicious
open-source packages are extensions hosted in the Open VSX repository that
claim to provide support for the Solidity programming language. However, in
practice, they download and execute malicious code on users' devices.
Extension description in the Open VSX repository
During an incident response, a blockchain developer from Russia reached out to Kaspersky after installing one of these fake extensions on his computer, which allowed attackers to steal approximately $500,000 worth of crypto assets.
The threat actor
behind these packages managed to deceive the developer by making the malicious
package rank higher than the legitimate one. The attacker achieved this by
artificially inflating the malicious package’s downloads count to 54,000.
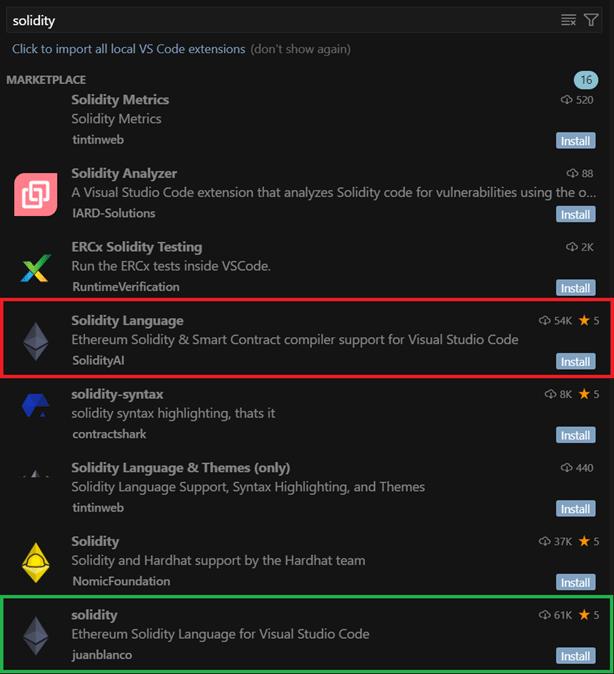
Search results for the query “solidity”: the malicious extension
(highlighted in red) and the legitimate one (highlighted in green).
After installation,
the victim gained no actual functionality from the extension. Instead,
malicious ScreenConnect software was installed on the computer, granting threat
actors remote access to the infected device. Using this access, they deployed
the open-source Quasar backdoor along with a stealer that collects data from
browsers, email clients, and crypto wallets. With these tools, the threat
actors were able to obtain the developer’s wallet seed phrases and subsequently
steal cryptocurrency from the accounts.
After the malicious
extension downloaded by the developer was discovered and removed from the
repository, the threat actor republished it and artificially inflated its
installation count to a higher number – 2 million, compared to 61,000 for the
legitimate package. The extension was removed from the platform following a
request from Kaspersky.

New malicious extension on Open VSX
“Spotting compromised open-source packages with the naked eye is
becoming increasingly difficult. Threat actors are using increasingly
creative tactics to deceive potential victims, even developers who have a
strong understanding of cybersecurity risks — particularly those working in the
blockchain development field. As we expect adversaries to continue targeting
developers, it is recommended that even experienced IT professionals deploy
dedicated security solutions to safeguard sensitive data and prevent financial
losses.” commented Georgy Kucherin, Security Researcher with
Kaspersky’s Global Research and Analysis Team.
The threat actor behind the attack published not only malicious Solidity extensions but also another NPM package, solsafe, which also downloads ScreenConnect. A few months earlier, three additional malicious Visual Studio Code extensions were released — solaibot, among-eth, and blankebesxstnion — all of them have already been removed from the repository.
More information is
available in a report on Securelist.com.
To stay safe,
Kaspersky recommends:
- Use a solution for monitoring the used
open-source components in order to detect the threats that might be hidden
inside.
- If you suspect that a threat actor may have gained access to your company’s
infrastructure, we recommend using the Kaspersky Compromise Assessment service
to uncover any past or ongoing attacks.
- Verify package maintainers: check the credibility of the maintainer or
organization behind the package. Look for consistent version history,
documentation, and an active issue tracker.
- Stay informed on emerging threats: subscribe to security bulletins and
advisories related to the open-source ecosystem. The earlier you know about a
threat, the faster you can respond.




