Kaspersky detected a complex attack sequence that involved retrieving information from legitimate services such as GitHub, Microsoft Learn Challenge, Quora, and social networks. The attackers did this to avoid detection and run an execution chain to launch Cobalt Strike Beacon, a tool to remotely control computers, execute commands, steal data, and maintain persistent access within a network. The attacks were detected in the second half of 2024 in organizations across China, Japan, Malaysia, Peru and Russia, and persisted into 2025. The majority of victims were large to medium-sized businesses.
To infiltrate victims’ devices, the attackers sent spear phishing emails which were disguised as legitimate communications from major state-owned companies, particularly within the oil and gas sector. The text was phrased to look like there was interest in products and services of the victim organization to convince the recipient to open the malicious attachment. The attachment was an archive with what looked like PDF files containing requirements for the requested products and services – but in fact some of these PDFs were executable EXE and DLL files containing malware.
The attackers leveraged DLL highjacking techniques and exploited the legitimate Crash reporting Send Utility which is originally designed to help developers get detailed, real-time crash reports for their applications. To function, the malware also retrieved and downloaded a code that was stored in public profiles on popular legitimate platforms to avoid detection. Kaspersky found this code encrypted inside profiles on GitHub, and links to it (also encrypted) – on other GitHub profiles, Microsoft Learn Challenge, Q&A websites, and even Russian social media platforms. All of these profiles and pages were created specifically for this attack. After the malicious code was executed on victims’ machines, Cobalt Strike Beacon was launched, and the victims’ systems were compromised.
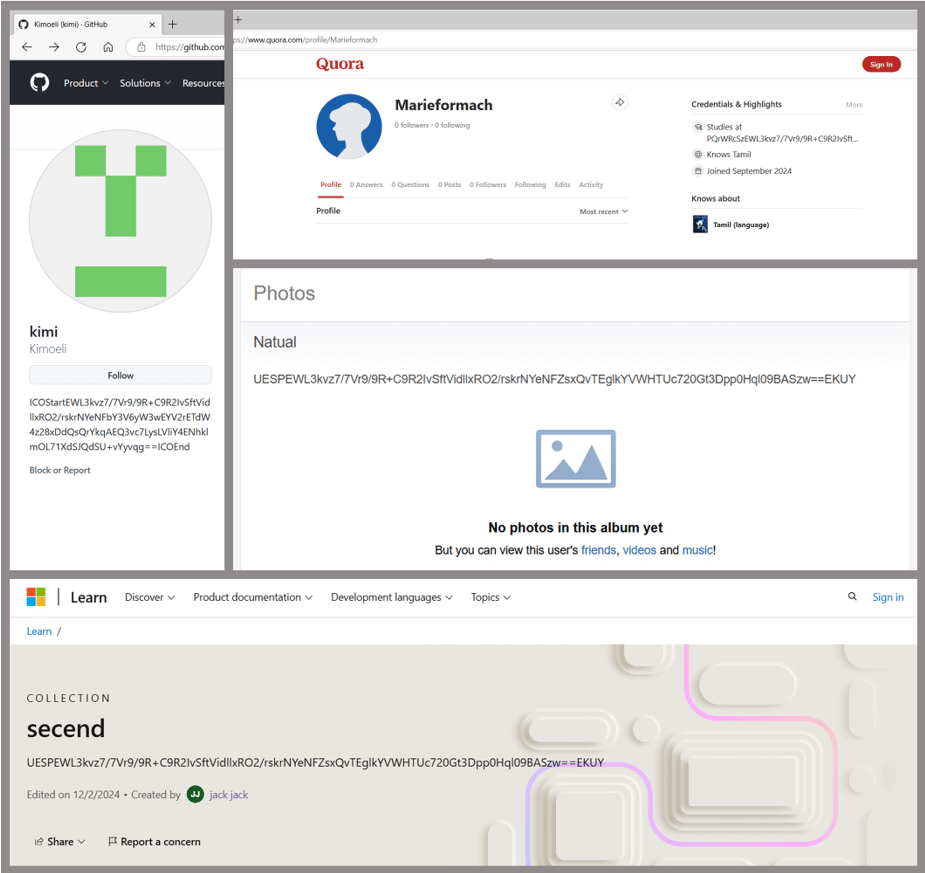
Profiles on popular online platforms containing malicious code
“While we didn't find any evidence of the attackers using real people's social media profiles, as all the accounts were created specifically for this attack, there's nothing stopping the threat actor from abusing various mechanisms these platforms provide. For instance, malicious content strings could be posted in comments on legitimate users' posts. Threat actors are using increasingly complex methods to conceal long-known tools, and it’s important to stay up to date with the latest threat intelligence to be protected from such attacks,” comments Maxim Starodubov, Malware Analyst Team Lead at Kaspersky.
The method used to retrieve the download address for the malicious code is similar to what was observed in the EastWind campaign linked to Chinese-speaking actors.
More details are available on Securlist.com.
Kaspersky recommends that organizations follow these security guidelines to stay safe:
- Track the status of digital infrastructure and continuously monitor the perimeter.
- Use proven security solutions to detect and block malware embedded within bulk email.
- Train staff to increase cybersecurity awareness.
- Secure corporate devices with a comprehensive system that detects and blocks attacks in the early stages




