Kaspersky Global Research and Analysis Team (GReAT) discovered a new version of the Zanubis mobile banking trojan targeting users in Peru. When Zanubis originally emerged in 2022, it mimicked PDF readers or Peru government organizations’ apps, and now in 2025 it disguises itself as two new apps – one of a local company in the energy sector and the other – of a local bank. With advanced social engineering techniques, users are persuaded to download and install these fake apps, which steal banking credentials and keys from digital or crypto wallets. Zanubis also performs keylogging and screen recording, among other functionality. Kaspersky detected over 130 victims in the latest campaign, and about 1,250 since the monitoring of this malware started.
On smartphones running
Android, apps can be installed from different stores, but they can also be
installed directly from APK files bypassing the stores. Zanubis made its way
onto victims’ smartphones through APK files. When mimicking the energy company,
the malicious APK is distributed under names such as “Boleta_XXXXXX.apk”
("Bill") or “Factura_XXXXXX.apk” ("Invoice"), deceiving
users into believing they are opening and verifying an alleged bill or invoice.
These apps pose as fake invoice verification tools, requiring users to install
them and enter their customer information in order to check for various
outstanding invoices. Meanwhile, when mimicking the bank, victims are tricked
into downloading the malware under the guise of instructions from a fake bank
advisor.
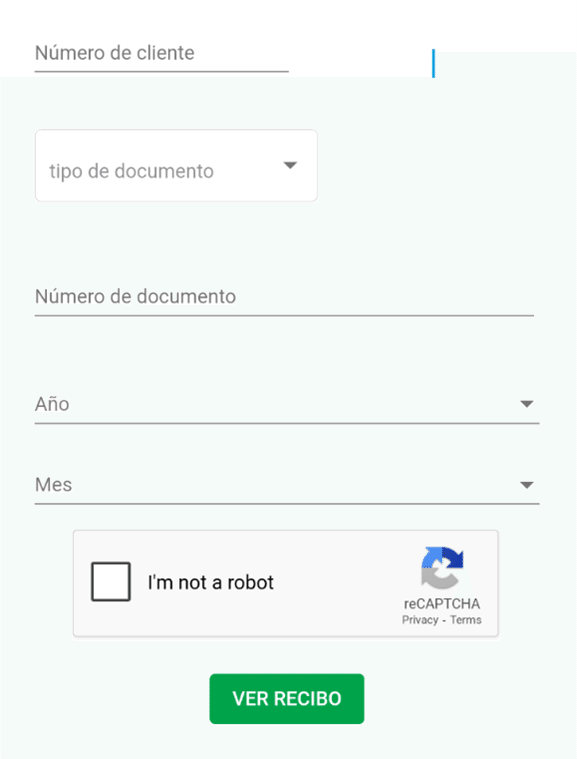
A fake form inside the app to verify invoices
Once the user downloads and launches any of the described APK files, a screen appears with the organization’s deceptively used logo, stating that necessary checks are in progress. The app requires the user to give accessibility permissions claiming that they are necessary for the app’s normal operation.
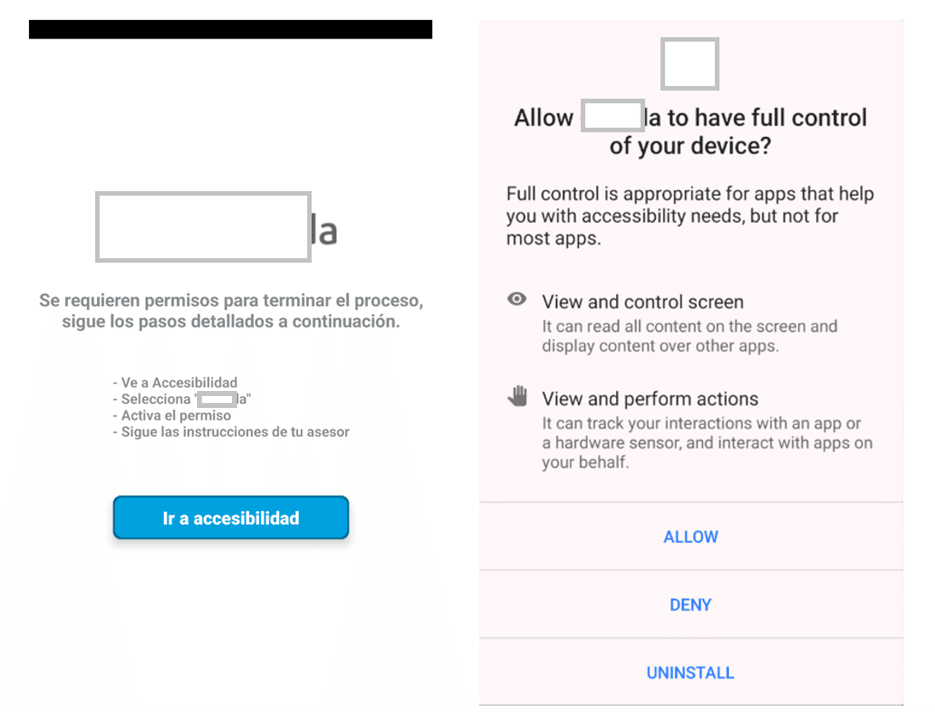
Screenshots of the malicious app requesting
accessibility permissions
Android accessibility
permissions grant apps the ability to interact with and control various aspects
of the device’s interface and functionality, primarily to assist users with
disabilities. When a malware app gains accessibility permissions, attackers can
covertly monitor and capture sensitive user data, such as passwords, messages,
and banking details, by reading screen content and notifications. This is
exactly what attackers behind Zanubis did to steal funds and get access to
other private information.
The threat actors
behind Zanubis are likely to be operating from Peru. There is consistent use of
Latin American Spanish in the code, and the attackers demonstrate knowledge of
Peruvian banking and government agencies.
“Zanubis has
demonstrated a clear evolution, transitioning from a simple banking Trojan to a
highly sophisticated and multi-faceted threat. Its focus remains on high-value
targets, particularly banks and financial institutions in Peru. The attackers
behind Zanubis show no signs of slowing down. They continue to adjust their
tactics, shifting distribution methods to ensure the malware reaches new
victims and executes silently. It is crucial for individual and corporate users
and to stay vigilant and boost their digital literacy levels, as well as use
trusted and proven security solutions, to avoid such threats,” commented
Leandro Cuozzo, Security Researcher with Kaspersky’s Global Research and
Analysis Team.
More information is
available in a report on Securelist.com.
To protect yourself
from mobile threats, Kaspersky recommends:
- Download apps only
from official app stores for smartphones, such as Apple App Store and Google
Play, but remember that even downloading apps from official stores is not
always risk-free. Kaspersky recently discovered SparkCat, the first
screenshot-stealing malware to bypass the App Store's security. The malware was
also found on Google Play, with a total of 20 infected apps across both
platforms, proving that these stores are not 100% foolproof.
- To stay safe, always
check app reviews, use only links from official websites, and install reliable
security software, like Kaspersky Premium, that can
detect and block malicious activity if an app turns out to be fraudulent.
- Check the permissions
of apps that you use and think carefully before permitting an app, especially
when it comes to high-risk permissions such as Accessibility Services.
- Update your operating
system and important apps as updates become available. Many safety issues can
be solved by installing updated versions of software.
About the Global Research &
Analysis Team
Established in 2008,
Global Research & Analysis Team (GReAT) operates at the very heart of
Kaspersky, uncovering APTs, cyber-espionage campaigns, major malware,
ransomware and underground cyber-criminal trends across the world. Today GReAT
consists of 30+ experts working globally – in Europe, Russia, Latin America,
Asia and the Middle East. Talented security professionals provide company
leadership in anti-malware research and innovation, bringing unrivaled
expertise, passion and curiosity to the discovery and analysis of cyberthreats.




