Anti-Ransomware Day was established on May 12 in 2020 by INTERPOL in collaboration with Kaspersky to commemorate the anniversary of the infamous WannaCry ransomware attack that occurred on May 12, 2017. The purpose of Anti-Ransomware Day is to raise global awareness about the threats posed by ransomware and to promote best practices for prevention and response.
With International
Anti-Ransomware Day approaching on May 12, Kaspersky presents its annual report on the evolving global and
regional ransomware cyberthreat landscape.
According to Kaspersky
Security Network data, the Middle East, APAC and African
regions are leading by the share of users attacked by ransomware, with Latin
America, CIS (Commonwealth of Independent States) and Europe trailing behind.
Globally from 2023 to 2024 the share of users affected by ransomware attacks
increased to 0.44% by 0.02 p.p. The seemingly small
percentage is typical for ransomware and is explained by the fact that
attackers often don’t distribute this type of malware on a mass scale, but
prioritize high-value targets, which reduces the overall number of incidents.
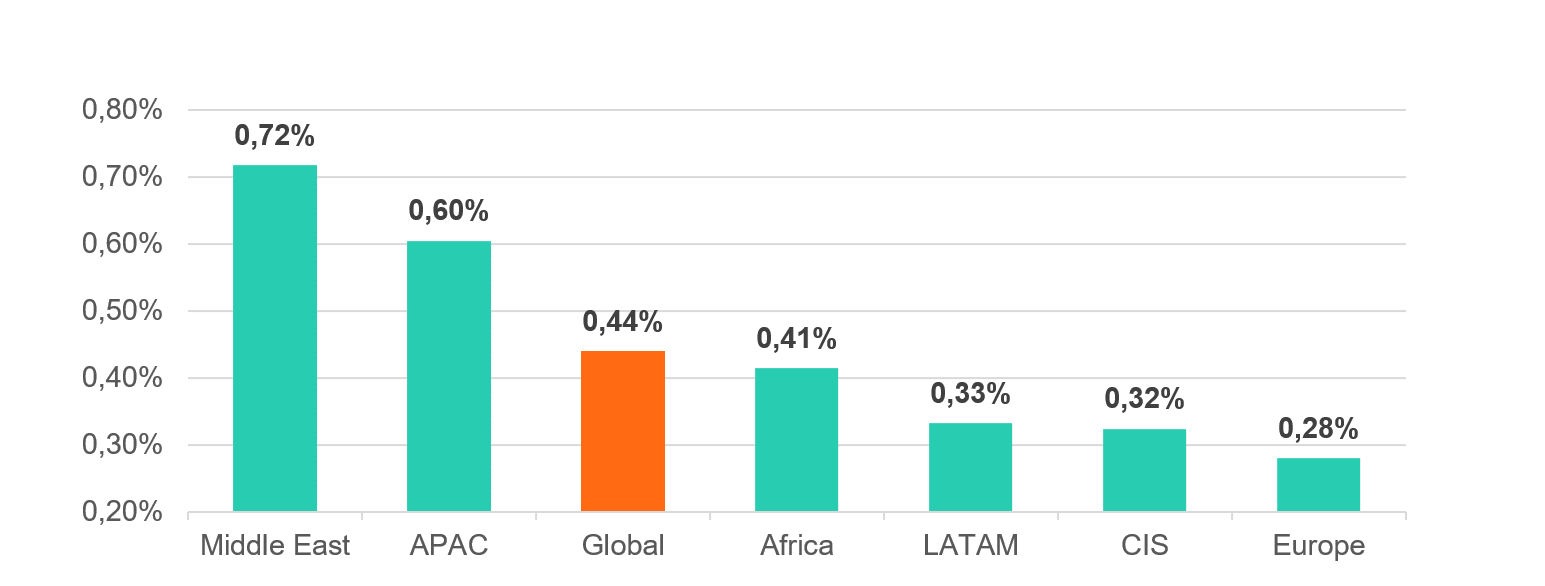
Share of users whose computers were attacked by crypto-ransomware,
by region
Data from Kaspersky Security Network
In the Middle East and Asia-Pacific regions,
ransomware affected a higher share of users due to rapid digital
transformation, expanding attack surfaces and varying levels of cybersecurity
maturity. Enterprises in APAC were heavily targeted, driven by attacks on
infrastructure and operational technology, especially in countries with growing
economies and new data privacy laws.
Ransomware is less
prevalent in Africa due to lower levels of
digitization and economic constraints, which reduce the number of high-value
targets. However, as countries like South Africa and Nigeria expand their
digital economies, ransomware attacks are on the rise, particularly in the
manufacturing, financial and government sectors. Limited cybersecurity
awareness and resources leave many organizations vulnerable, though the smaller
attack surface means the region remains behind global hotspots.
Latin America also experiences ransomware attacks,
particularly in Brazil, Argentina, Chile and Mexico. Manufacturing, government,
and agriculture, as well as critical sectors such as energy and retail are
targeted, but economic constraints and smaller ransoms deter some attackers.
Despite this, the region’s growing digital adoption is increasing exposure.
The Commonwealth of Independent States sees a smaller
share of users encountering ransomware attacks. However, hacktivist groups such
as Head Mare, Twelve and others active in the region often
use ransomware such as LockBit 3.0 to inflict damage on target organizations.
Manufacturing, government and retail sectors are the most targeted, with
varying levels of cybersecurity maturity across the region affecting
security .
Europe is consistently targeted with ransomware
but benefits from robust cybersecurity frameworks and regulations that deter
some attackers. Sectors such as manufacturing, agriculture, and education are
often targeted, but mature incident response and awareness limit the scale of
attacks. The region’s diversified economies and strong defenses make it less of
a focal point for ransomware groups than regions with rapid, less secure
digital growth.
Current and emerging ransomware
trends
AI tools were increasingly used
in ransomware development,
as demonstrated by FunkSec, a ransomware group that emerged in late 2024 and
quickly gained notoriety by surpassing established groups like Cl0p and
RansomHub with multiple victims claimed in December alone. Operating under a
Ransomware-as-a-Service (RaaS) model, FunkSec employs double extortion tactics
— combining data encryption with exfiltration — targeting sectors such as
government, technology, finance, and education in Europe and Asia. The group’s
heavy reliance on AI-assisted tools sets it apart, with its ransomware
featuring AI-generated code, complete with flawless comments, likely produced
by Large Language Models (LLMs) to enhance development and evade detection.
Unlike typical ransomware groups demanding millions, FunkSec adopts a
high-volume, low-cost approach with unusually low ransom demands, further
highlighting its innovative use of AI to streamline operations.
The RaaS
(Ransomware-as-a-Service) model remains the predominant framework for
ransomware attacks, fueling their
proliferation by lowering the technical barrier for cybercriminals. In 2024,
RaaS platforms like RansomHub thrived by offering malware, technical support
and affiliate programs that split the ransom. This model enables less-skilled
actors to execute sophisticated attacks, contributing to the emergence of
multiple new ransomware groups in 2024 alone.
In 2025, ransomware is expected
to evolve by exploiting unconventional vulnerabilities, as demonstrated by the Akira gang’s use of a webcam to bypass endpoint
detection and response systems and infiltrate internal networks. Attackers are
likely to increasingly target overlooked entry points like IoT devices, smart
appliances or misconfigured hardware in the workplace, capitalizing on the
expanding attack surface created by interconnected systems. As organizations
strengthen traditional defenses, cybercriminals will refine their tactics,
focusing on stealthy reconnaissance and lateral movement within networks to
deploy ransomware with greater precision, making it harder for defenders to
detect and respond in time.
The proliferation of LLMs
tailored for cybercrime will further amplify ransomware's reach and impact. LLMs marketed on the dark web lower the
technical barrier to creating malicious code, phishing campaigns and social
engineering attacks, allowing even less skilled actors to craft highly
convincing lures or automate ransomware deployment. As more innovative concepts
such as RPA (Robotic Process Automation) and LowCode, which provide an intuitive, visual, AI-assisted
drag-and-drop interface for rapid software development, are quickly adopted by
software developers, we can expect ransomware developers to use these tools to
automate their attacks as well as new code development, making the threat of
ransomware even more prevalent.
“Ransomware is one of the most pressing cybersecurity threats
facing organizations today, with attackers targeting businesses of all sizes
and across every region. In our report we highlight that there is a concerning
shift toward exploiting overlooked entry points — including IoT devices, smart
appliances, and misconfigured or outdated workplace hardware. These weak spots
often go unmonitored, making them prime targets for cybercriminals. To stay
secure, organizations need a layered defense: up-to-date systems, network
segmentation, real-time monitoring, robust backups, and continuous user
education. Building cyber awareness at every level is just as important as
investing in the right technology,” comments Dmitry Galov, Head of
Research Center for Russia and CIS at Kaspersky's GReAT.
Read the report
on Securelist.com for the more information
about ransomware trends in 2025.
On Anti-Ransomware
Day and beyond, Kaspersky encourages organizations to follow these best
practices to safeguard from ransomware:
-
Enable ransomware
protection for all endpoints. There is a free Kaspersky Anti-Ransomware Tool for Business that
shields computers and servers from ransomware and other types of malware,
prevents exploits and is compatible with already installed security solutions.
- Always keep software
updated on all the devices you use to prevent attackers from exploiting
vulnerabilities and infiltrating your network.
- Focus your defense
strategy on detecting lateral movements and data exfiltration to the internet.
Pay special attention to outgoing traffic to detect cybercriminals’ connections
to your network. Set up offline backups that intruders cannot tamper with. Make
sure you can access them quickly when needed or in an emergency.
- Install anti-APT and
EDR solutions, enabling capabilities for advanced threat discovery and
detection, investigation and timely remediation of incidents. Provide your SOC
team with access to the latest threat intelligence and regularly upskill them
with professional training. All of the above is available within Kaspersky Expert Security framework.
- Use the latest Threat Intelligence information
to stay aware of the actual Tactics, Techniques, and Procedures (TTPs) used by
threat actors.
- To protect the company
against a wide range of threats, use solutions from Kaspersky
Next product line that provide real-time protection, threat
visibility, investigation and response capabilities of EDR and XDR for
organizations of any size and industry. Depending on your current needs and
available resources, you can choose the most relevant product tier and easily
migrate to another one if your cybersecurity requirements are changing.




