At the Security Analyst Summit 2016 our Global Research and Analysis Team (GReAT) has published extensive research on the Adwind Remote Access Tool (RAT). This malicious tool is also known as AlienSpy, Frutas, Unrecom, Sockrat, JSocket and jRat. It has been developed for several years and distributed through a single malware-as-a-service platform, which means that anyone can pay small dollars (from $25 to $300) for the service and use the malicious tool to their advantage.
Our GReAT researchers discovered this malware platform during the attempted targeted attack against a bank in Singapore. The malware came in form of a malicious Java-file attached to a spear-phishing email, which was received by a targeted employee at the bank. Basically, it was a typical example of how this malware can be distributed.
Several features of this malware piqued the attention of the researchers. First of all, it was able to run on multiple platforms: aside from Windows it could infect Linux, OS X and Android operating systems. Though Java is not a common platform for malware at all, it is still considered the second biggest security vulnerability that requires constant patching, while the first is definitely Adobe’s Flash plugin. Moreover, Java applications by design are capable of running on any operational system. This makes Java very convenient surrounding for those who want to develop multi-platform malware. This is basically why Oracle is really putting a lot of effort into improving Java’s security.
Oracle to Kill Java Browser Plugin: https://t.co/aF0qj9WWWV via @threatpost #RIPJAVA pic.twitter.com/5kbts0mNcD
— Kaspersky (@kaspersky) January 28, 2016
The second thing that stood out of the malware discovery was that it was not picked up by any anti-virus program.Thirdly, it was very capable: the list of its functions included the ability to collect keystrokes; steal cached passwords, VPN certificates and cryptocurrencies wallets’ keys; take screenshots; record video, photos and sound from computer’s microphone and webcam; collect user and system information; manage SMS in case of Android OS, and so on. As you see, the only thing that limited criminals was their skills and imagination.
Shortlist of JSocket features. Only *short* list #TheSAS2016 pic.twitter.com/9SYObtskbZ
— Eugene Kaspersky (@e_kaspersky) February 8, 2016
All in all, it’s a very mighty multi-platform spying tool. After investigation of the malware’s activity our researchers came to the conclusion that the very story of Adwind malicious toolkit is far more thrilling than it might seem at the beginning.It turned out, that this malware is being developed for several years, with first samples dating back to 2012. At different periods of time it had different names: its creators branded it as Frutas in 2012, as Adwind in 2013, as Unrecom and AlienSpy in 2014 and as JSocket in 2015.
AlienSpy RAT Resurfaces as JSocket via @threatpost https://t.co/5ZWmhpGiKm pic.twitter.com/koTpglGJjP
— Kaspersky (@kaspersky) August 24, 2015
GReAT experts believe that there is only one hardworking individual behind the Adwind platform, who has been developing and supporting new features and modules for at least the last four years. Despite all the fuss about Java security, the platform was not created to make cybercriminal’s life easier, and the author of the Adwind malware had to come up with a number of workarounds to make the whole scheme work. Of course, this person might also pass some tasks to the shoulders of outsourcers, but all the efforts seem to be covered by a good revenue: as far as we calculated, the whole service might bring $200,000 per year. Still you should take into account that the latest version of the portal was started only in summer 2015 so the criminal might still be waiting for the money.
In the beginning the platform had only a Spanish interface, but later it got an English interface. With that update Adwind became recognized globally by cybercriminals of all stripes, including scammers performing advanced frauds, unfair business competitors, cyber-mercenaries who are hired to spy on people and organizations. It can also be used by anyone who wants to spy on people that they know.
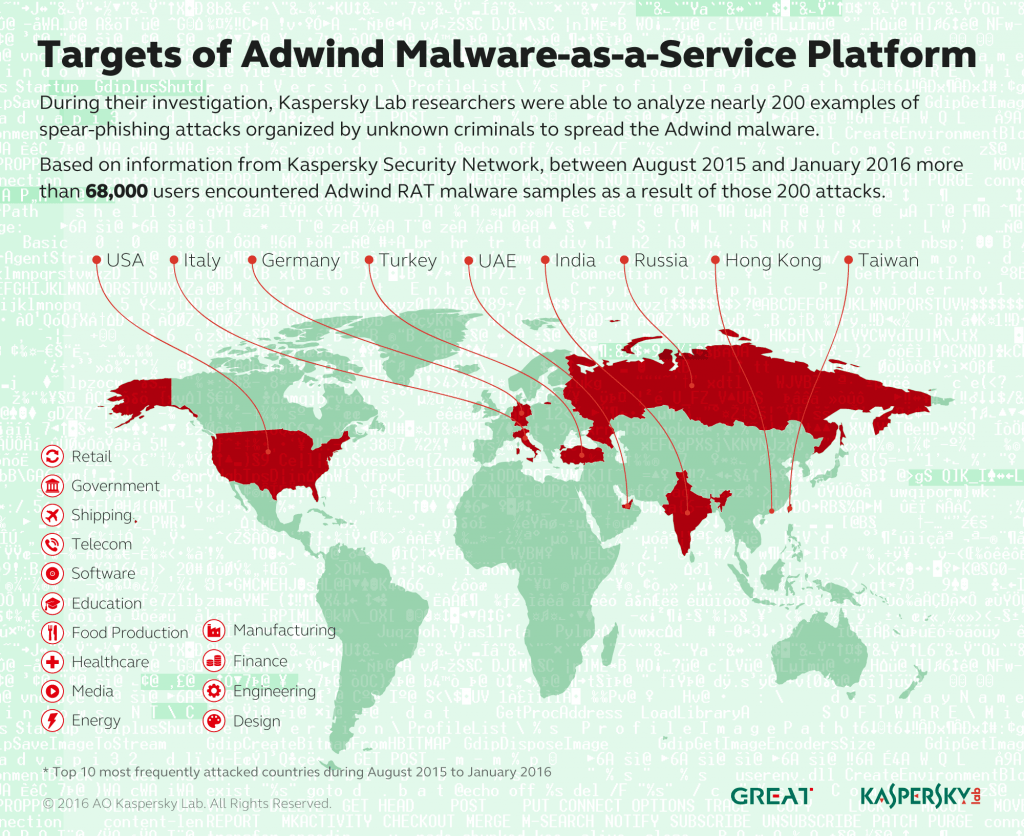
The geography of victims also changed during these years. In 2013 Arabic and Spanish-speaking countries were under fire. The next year criminals aimed at Turkey and India, followed by UAE, the US and Vietnam. In 2015 Russia was at the top, with UAE, Turkey, USA and Germany next to it. It is understandable, as now Adwind is sold to different cyberciminals who live around the world.
As far as we know, there were more than 443 thousand victims during these four years. It’s also noteworthy that we observed a large spike of infections in the end of 2015. Since August 2015 to January 2016 more than 68,0000 users encountered Adwind RAT malware samples. Moreover, in August 2015 this malware popped up in a cyber espionage story. It turned out, that one of Adwind solutions named AlienSpy had been used to spy on an Argentinian prosecutor, who was found dead in his apartment under mysterious circumstances, in January 2015.
.@vkamluk + @codelancer describing #Adwind, a cross-platform RAT found in some banks in Singapore. #TheSAS2016 pic.twitter.com/cu5myoF0kR
— Securelist (@Securelist) February 8, 2016
Criminals who bought and used Adwind kit targeted private individuals and small and medium businesses from a number of industries, including: manufacturing, finance, engineering, design, retail, government, shipping, telecom and a lot of others.That’s why we can’t but encourage enterprises to review the purpose of using Java platform and disable it for all unauthorized sources.
 Adwind
Adwind

 Tips
Tips