Virtually every employee of a large company comes across the occasional e-mail aiming to steal their corporate credentials. It’s usually in the form of mass phishing, an attack in which e-mails are sent out at random in the hope that at least some recipients will take the bait. However, the stream of phishing e-mails may contain one or two more dangerous, targeted messages, the content of which has been customized for employees of specific companies. This is spear-phishing.
Spear-phishing messages represent a clear sign that cybercriminals are interested in your company, specifically, and it may not be the only attack in play. That is a major reason infosec officers need to know if any employee has received a spear-phishing e-mail — they need to prepare countermeasures and alert personnel in good time.
That’s why we advise IT to check filtered e-mails periodically in search of spear-phishing, and to teach other employees how to spot signs of targeted phishing. What follows are a few of the most common tricks, with examples from some fresh spear-phishing campaigns.
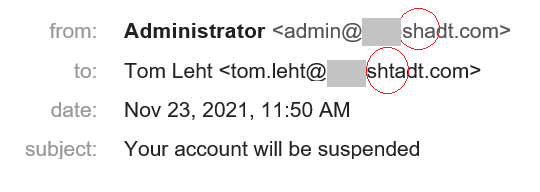
Misspelled company name
The human brain does not always perceive the whole of a written word — it sees a familiar beginning and completes the rest by itself. Attackers can take advantage of this trait by registering a domain that differs from your company’s by just one or two letters.
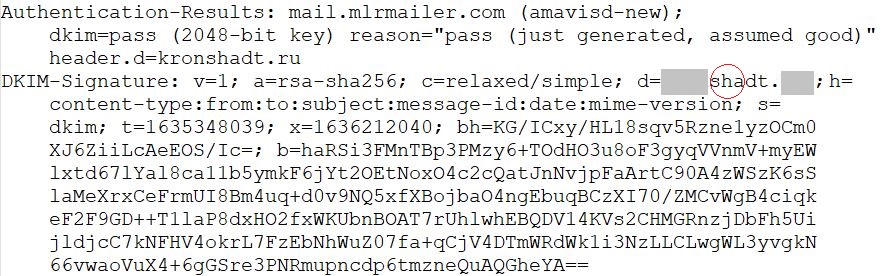
The cybercriminals who own the domain can even set up a DKIM signature so that the e-mail passes all checks — it’s their domain, after all.
Extra words in the company name
Another way to fool recipients into thinking a colleague is at the other end is to register a two-word domain, for example, to appear as a sender from a local branch or a particular department. In the latter case, cybercriminals tend to impersonate tech support or security personnel.
In reality, employees from every department should have a standard corporate e-mail address. No one ever sets up a separate domain for security personnel. As for local offices, if you’re not sure, check the domain in the corporate address book.
Specific content
A phishing e-mail mentioning your company (or worse, the recipient) by name is a sure sign of spear-phishing and a reason to sound the alarm.
Highly specialized topic
Strictly speaking, seeing those names doesn’t always mean a message is spear-phishing — it might be a variation on a mass-phishing scam. For example, phishers may use a database of conference participants’ addresses and play on the topic of the conference — that’s mass phishing. If they try to attack employees of a particular company in the exact same way, however, that’s spear-phishing, and thus security needs to know about it.
Finally, to be able to search for potential spear-phishing signs without diminishing the company’s actual security, we recommend installing protective antiphishing solutions on mail servers as well as on employee workstations.
 phishing
phishing


 Tips
Tips