Every year, scammers cook up new ways to trick people, and 2025 was no exception. Over the past year, our anti-phishing system thwarted more than 554 million attempts to follow phishing links, while our Mail Anti-Virus blocked nearly 145 million malicious attachments. To top it off, almost 45% of all emails worldwide turned out to be spam. Below, we break down the most impressive phishing and spam schemes from last year. For the deep dive, you can read the full Spam and Phishing in 2025 report on Securelist.
Phishing for fun
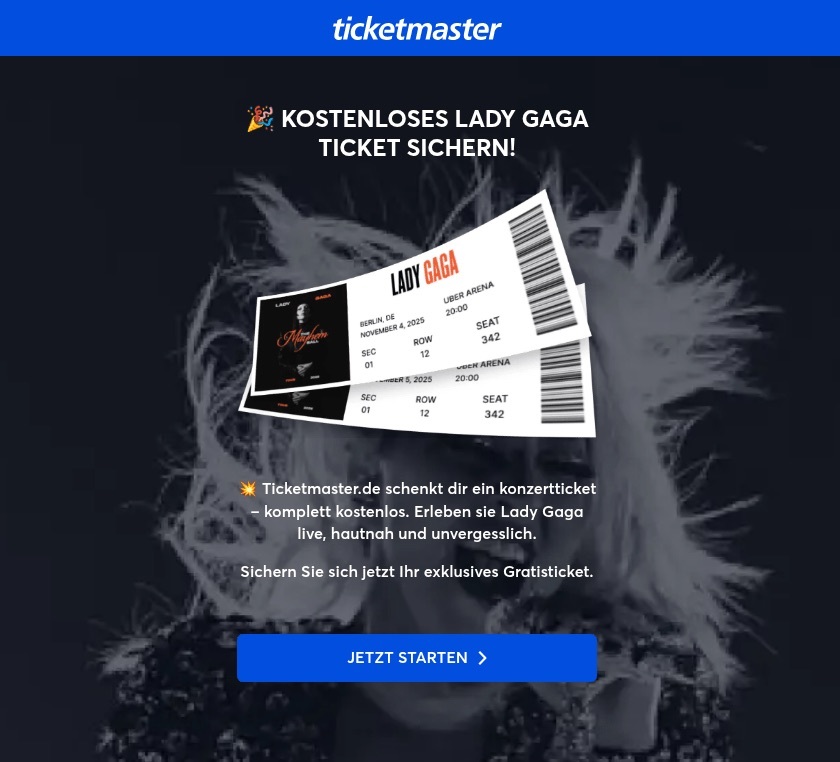
Music lovers and cinephiles were prime targets for scammers in 2025. Bad actors went all out creating fake ticketing aggregators and spoofed versions of popular streaming services.
On these fake aggregator sites, users were offered “free” tickets to major concerts. The catch? You just had to pay a small “processing fee” or “shipping cost”. Naturally, the only thing being delivered was your hard-earned cash straight into a scammer’s pocket.
With streaming services, the hustle went like this: users received a tempting offer to, say, migrate their Spotify playlists to YouTube by entering their Spotify credentials. Alternatively, they were invited to vote for their favorite artist in a chart — an opportunity most fans find hard to pass up. To add a coat of legitimacy, scammers name-dropped heavy hitters like Google and Spotify. The phishing form targeted multiple platforms at once — Facebook, Instagram, or email — requiring users to enter their credentials to vote hand over their accounts.
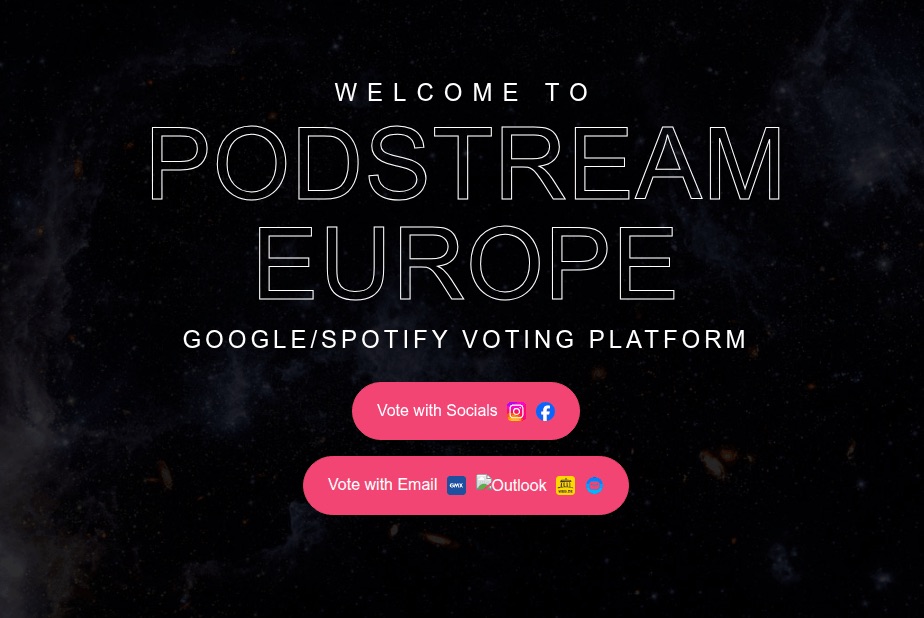
This phishing page mimicking a multi-login setup looks terrible — no self-respecting designer would cram that many clashing icons onto a single button
In Brazil, scammers took it a step further: they offered users the chance to earn money just by listening to and rating songs on a supposed Spotify partner service. During registration, users had to provide their ID for Pix (the Brazilian instant payment system), and then make a one-time “verification payment” of 19.9 Brazilian reals (about $4) to “confirm their identity”. This fee was, of course, a fraction of the promised “potential earnings”. The payment form looked incredibly authentic and requested additional personal data — likely to be harvested for future attacks.
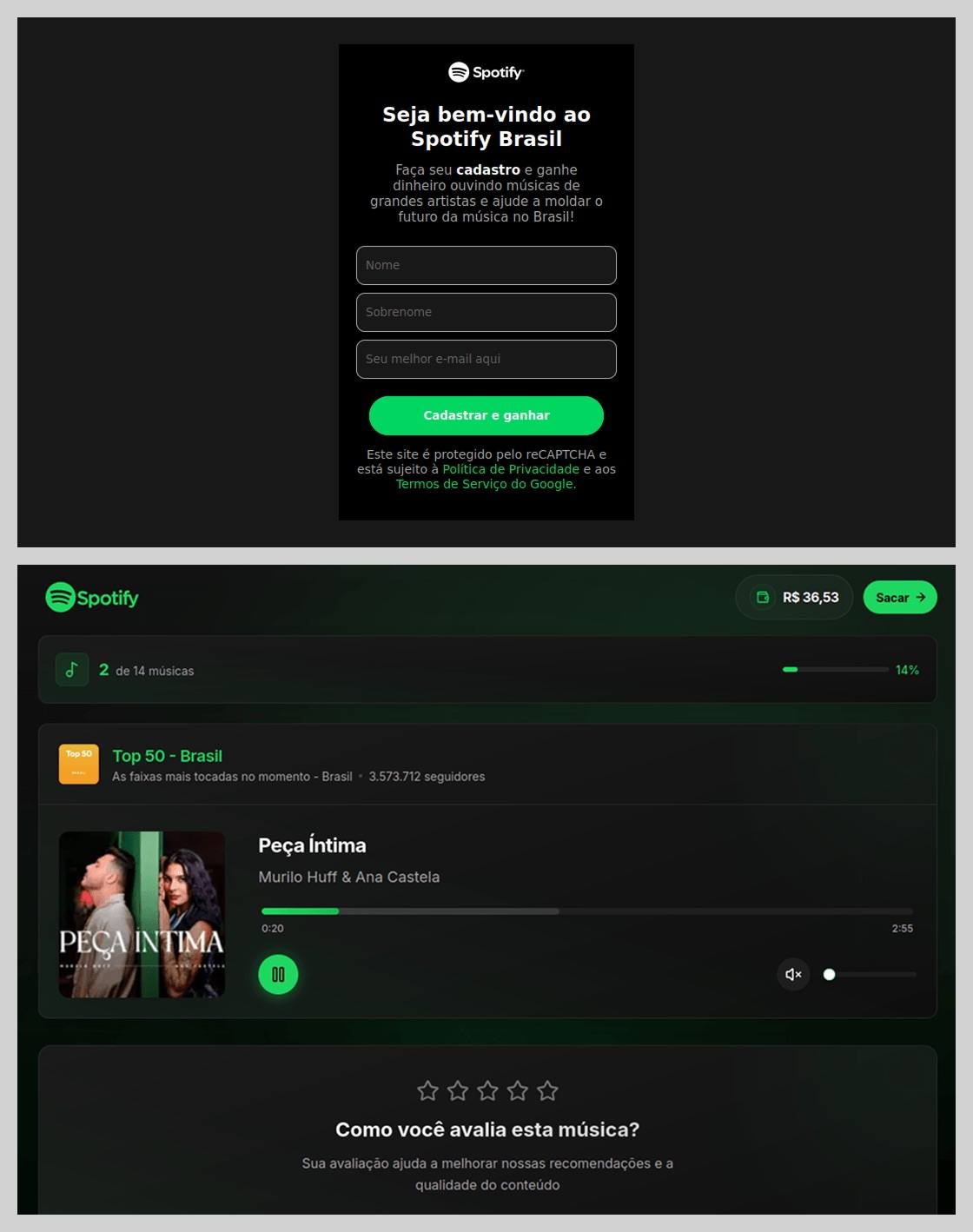
This scam posed as a service for boosting Spotify ratings and plays, but to start “earning”, you first had to pay up
The “cultural date” scheme turned out to be particularly inventive. After matching and some brief chatting on dating apps, a new “love interest” would invite the victim to a play or a movie and send a link to buy tickets. Once the “payment” went through, both the date and the ticketing site would vanish into thin air. A similar tactic was used to sell tickets for immersive escape rooms, which have surged in popularity lately; the page designs mirrored real sites to lower the user’s guard.
Phishing via messaging apps
The theft of Telegram and WhatsApp accounts became one of the year’s most widespread threats. Scammers have mastered the art of masking phishing as standard chat app activities, and have significantly expanded their geographical reach.
On Telegram, free Premium subscriptions remained the ultimate bait. While these phishing pages were previously only seen in Russian and English, 2025 saw a massive expansion into other languages. Victims would receive a message — often from a friend’s hijacked account — offering a “gift”. To activate it, the user had to log in to their Telegram account on the attacker’s site, which immediately led to another hijacked account.
Another common scheme involved celebrity giveaways. One specific attack, disguised as an NFT giveaway, stood out because it operated through a Telegram Mini App. For the average user, spotting a malicious Mini App is much harder than identifying a sketchy external URL.
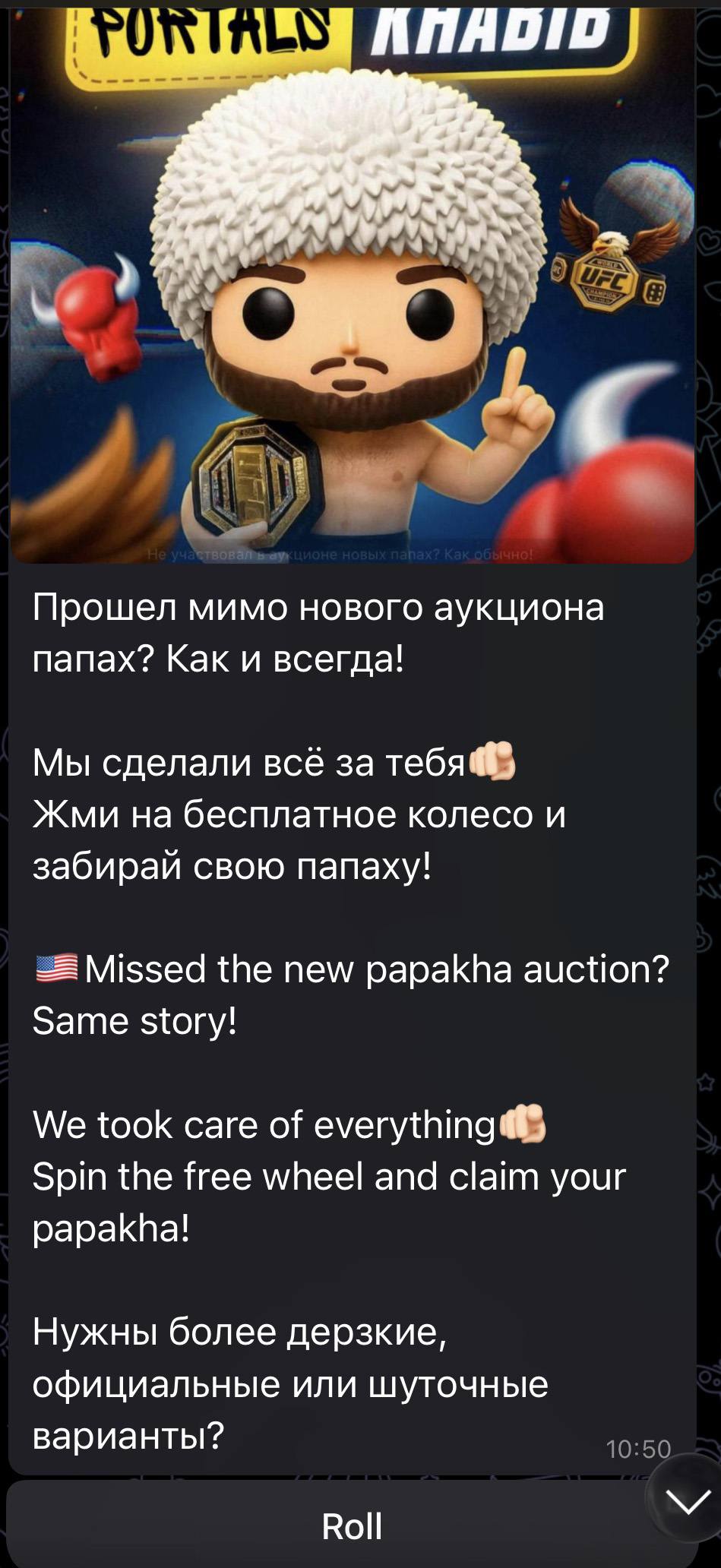
Scammers blasted out phishing bait for a fake Khabib Nurmagomedov NFT giveaway in both Russian and English simultaneously. However, in the Russian text, they forgot to remove a question from the AI that generated the text, “Do you need bolder, formal, or humorous options?” — which points to a rushed job and a total lack of editing
Finally, the classic vote for my friend messenger scam evolved in 2025 to include prompts to vote for the “city’s best dentist” or “top operational leader” — unfortunately, just bait for account takeovers.
Another clever method for hijacking WhatsApp accounts was spotted in China, where phishing pages perfectly mimicked the actual WhatsApp interface. Victims were told that due to some alleged “illegal activity”, they needed to undergo “additional verification”, which — you guessed it — ended up with a stolen account.
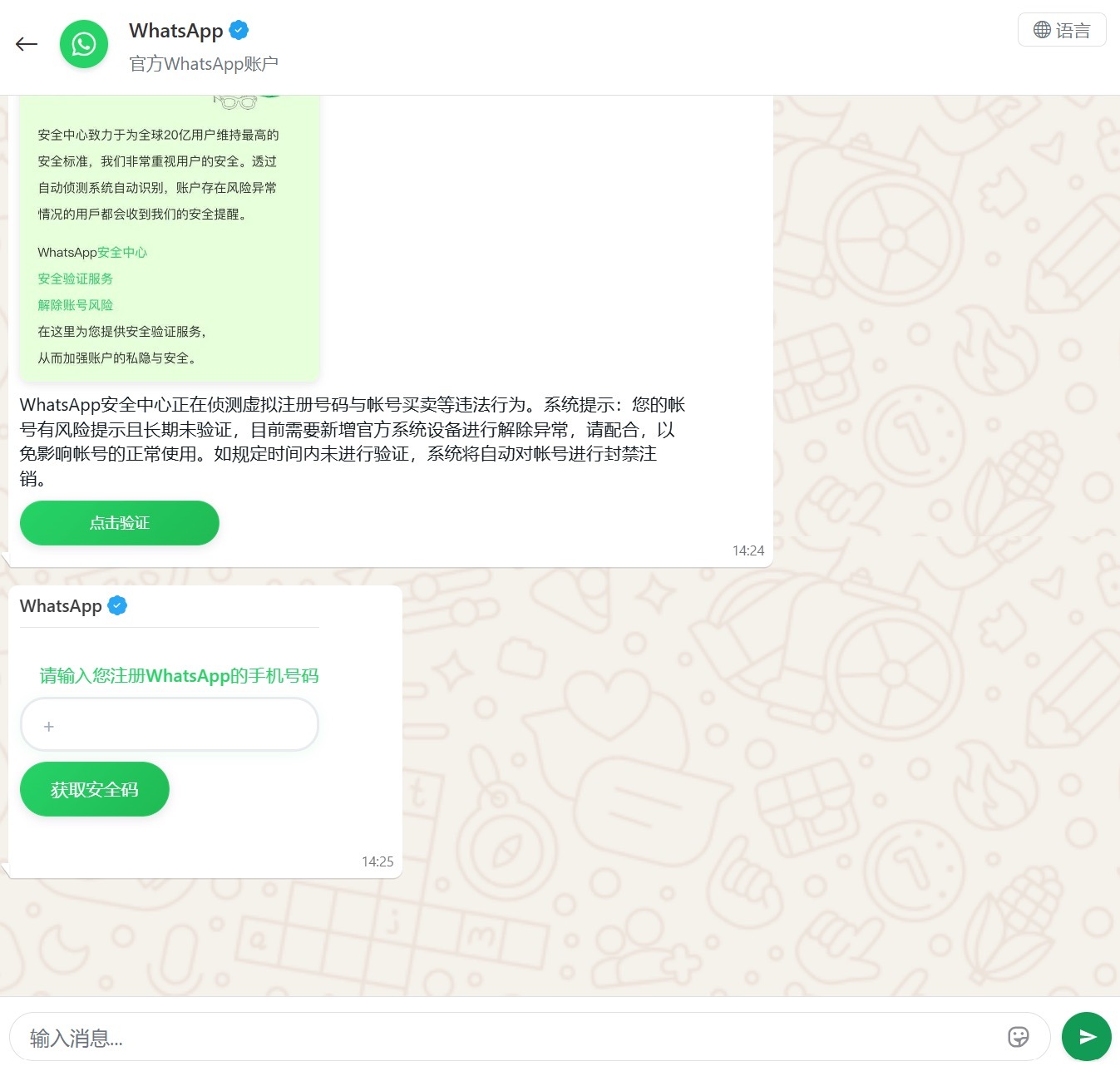
Victims were redirected to a phone number entry form, followed by a request for their authorization code
Impersonating Government Services
Phishing that mimics government messages and portals is a “classic of the genre”, but in 2025, scammers added some new scripts to the playbook.
In Russia, vishing attacks targeting government service users picked up steam. Victims received emails claiming an unauthorized login to their account, and were urged to call a specific number to undergo a “security check”. To make it look legit, the emails were packed with fake technical details: IP addresses, device models, and timestamps of the alleged login. Scammers also sent out phony loan approval notifications: if the recipient hadn’t applied for a loan (which they hadn’t), they were prompted to call a fake support team. Once the panicked victim reached an “operator”, social engineering took center stage.
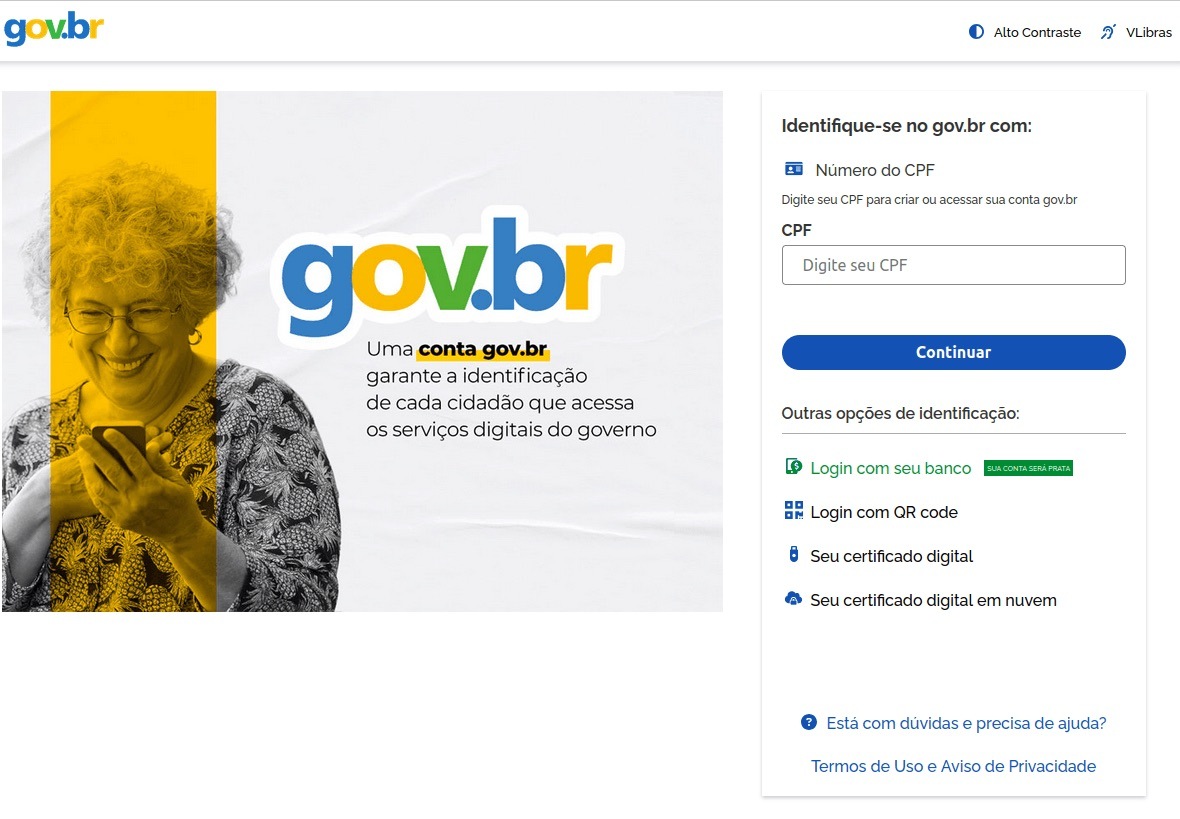
In Brazil, attackers hunted for taxpayer numbers (CPF numbers) by creating counterfeit government portals. Since this ID is the master key for accessing state services, national databases, and personal documents, a hijacked CPF is essentially a fast track to identity theft.
In Norway, scammers targeted people looking to renew their driver’s licenses. A site mimicking the Norwegian Public Roads Administration collected a mountain of personal data: everything from license plate numbers, full names, addresses, and phone numbers to the unique personal identification numbers assigned to every resident. For the cherry on top, drivers were asked to pay a “license replacement fee” of 1200 NOK (over US$125). The scammers walked away with personal data, credit card details, and cash. A literal triple-combo move!
Generally speaking, motorists are an attractive target: they clearly have money and a car and a fear of losing it. UK-based scammers played on this by sending out demands to urgently pay some overdue vehicle tax to avoid some unspecified “enforcement action”. This “act now!” urgency is a classic phishing trope designed to distract the victim from a sketchy URL or janky formatting.
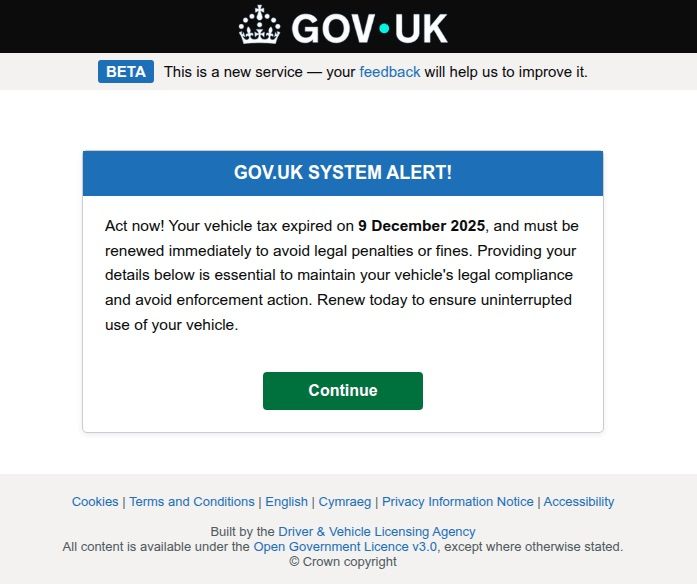
Scammers pressured Brits to pay purportedly overdue vehicle taxes “immediately” to keep something bad from happening
Let us borrow your identity, please
In 2025, we saw a spike in phishing attacks revolving around Know Your Customer (KYC) checks. To boost security, many services now verify users via biometrics and government IDs. Scammers have learned to harvest this data by spoofing the pages of popular services that implement these checks.
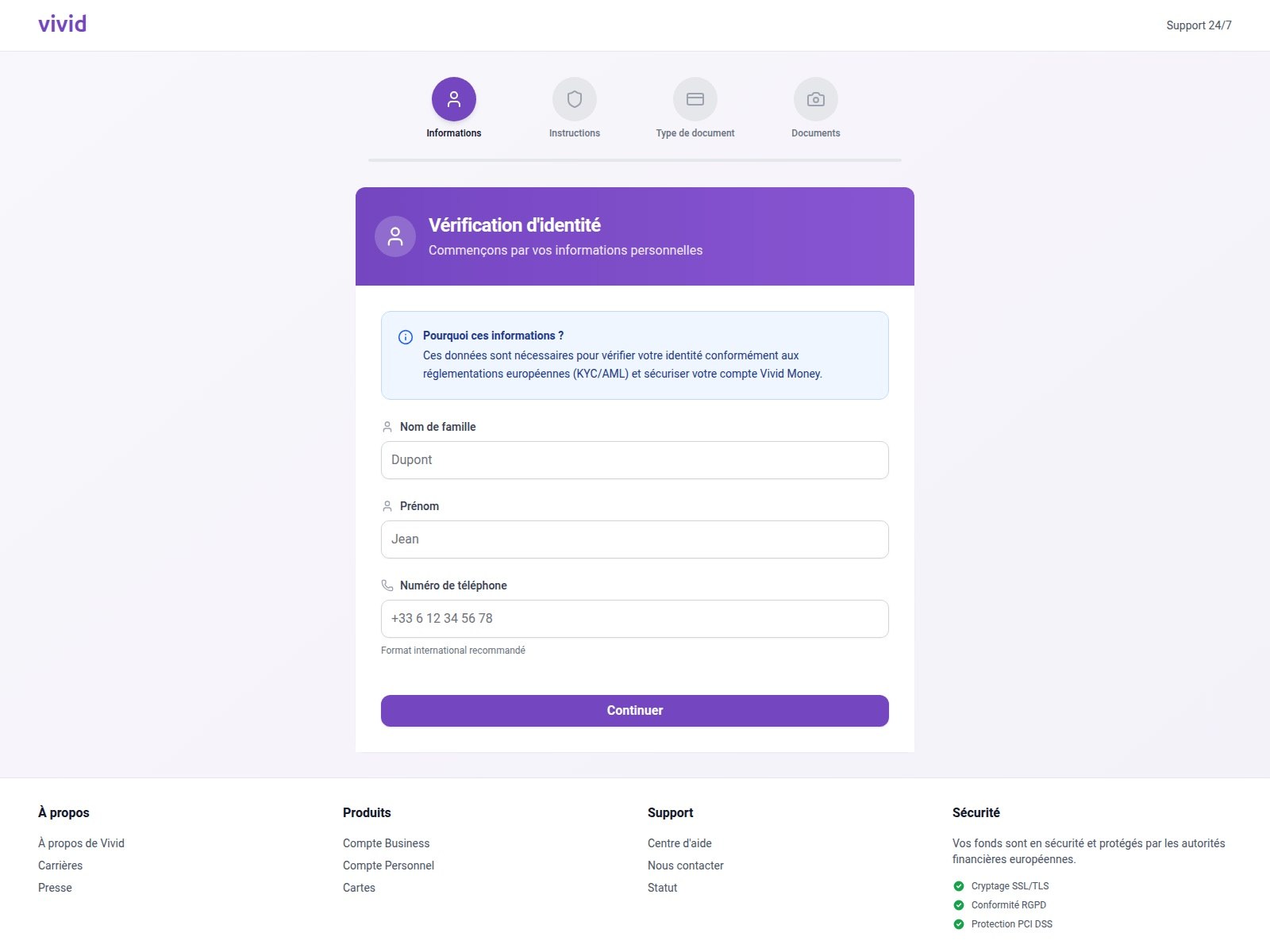
On this fraudulent Vivid Money page, scammers systematically collected incredibly detailed information about the victim
What sets these attacks apart is that, in addition to standard personal info, phishers demand photos of IDs or the victim’s face — sometimes from multiple angles. This kind of full profile can later be sold on dark web marketplaces or used for identity theft. We took a deep dive into this process in our post, What happens to data stolen using phishing?
AI scammers
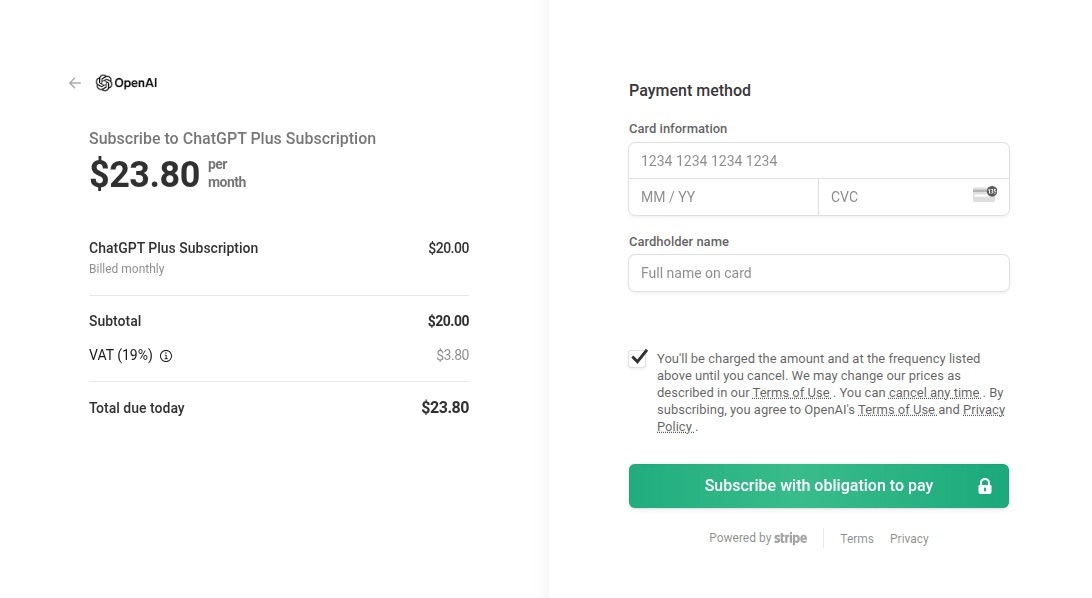
Naturally, scammers weren’t about to sit out the artificial intelligence boom. ChatGPT became a major lure: fraudsters built fake ChatGPT Plus subscription checkout pages, and offered “unique prompts” guaranteed to make you go viral on social media.
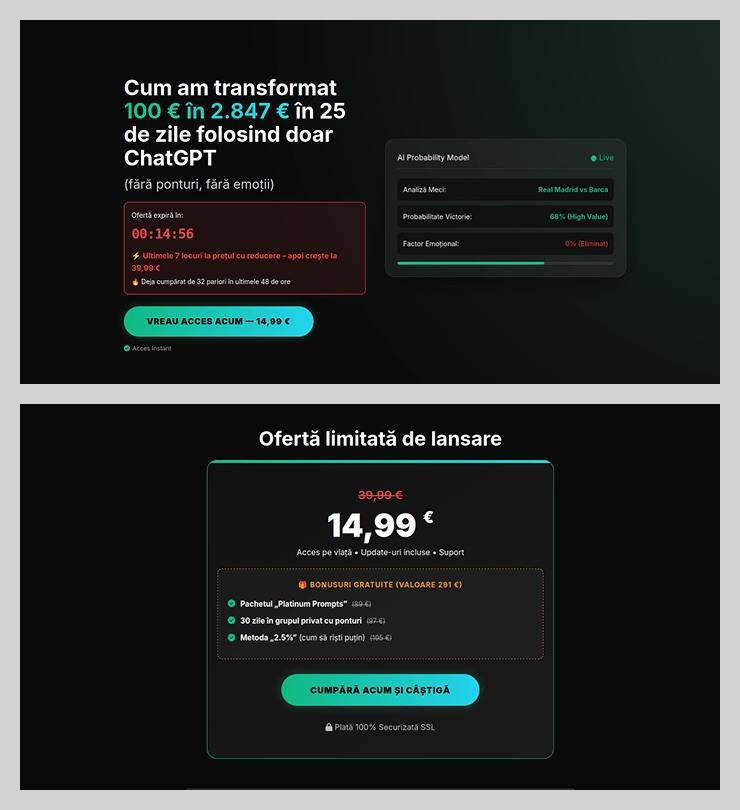
The “earn money with AI” scheme was particularly cynical. Scammers offered passive income from bets allegedly placed by ChatGPT: the bot does all the heavy lifting while the user just watches the cash roll in. Sounds like a dream, right? But to “catch” this opportunity, you had to act fast. A special price on this easy way to lose your money was valid for only 15 minutes from the moment you hit the page, leaving victims with no time to think twice.
Across the board, scammers are aggressively adopting AI. They’re leveraging deepfakes, automating high-quality website design, and generating polished copy for their email blasts. Even live calls with victims are becoming components of more complex schemes, which we detailed in our post, How phishers and scammers use AI.
Booby-trapped job openings
Someone looking for work is a prime target for bad actors. By dangling high-paying remote roles at major brands, phishers harvested applicants’ personal data — and sometimes even squeezed them for small “document processing fees” or “commissions”.
In more sophisticated setups, “employment agency” phishing sites would ask for the phone number linked to the user’s Telegram account during registration. To finish “signing up”, the victim had to enter a “confirmation code”, which was actually a Telegram authorization code. After entering it, the site kept pestering the applicant for more profile details — clearly a distraction to keep them from noticing the new login notification on their phone. To “verify the user”, the victim was told to wait 24 hours, giving the scammers, who already had a foot in the door, enough time to hijack the Telegram account permanently.
Hype is a lie (but a very convincing one)
As usual, scammers in 2025 were quick to jump on every trending headline, launching email campaigns at breakneck speed.
For instance, following the launch of $TRUMP meme coins by the U.S. President, scam blasts appeared promising free NFTs from “Trump Meme Coin” and “Trump Digital Trading Cards”. We’ve previously broken down exactly how meme coins work, and how to (not) lose your shirt on them.
The second the iPhone 17 Pro hit the market, it became the prize in countless fake surveys. After “winning”, users just had to provide their contact info and pay for shipping. Once those bank details were entered, the “winner” risked losing not just the shipping fee, but every cent in their account.
Riding the Ozempic wave, scammers flooded inboxes with offers for counterfeit versions of the drug, or sketchy “alternatives” that real pharmacists have never even heard of.
And during the BLACKPINK world tour, spammers pivoted to advertising “scooter suitcases just like the band uses”.
Even Jeff Bezos’s wedding in the summer of 2025 became fodder for “Nigerian” email scams. Users received messages purportedly from Bezos himself or his ex-wife, MacKenzie Scott. The emails promised massive sums in the name of charity or as “compensation” from Amazon.
How to stay safe
As you can see, scammers know no bounds when it comes to inventing new ways to separate you from your money and personal data — or even stealing your entire identity. These are just a few of the wildest examples from 2025; you can dive into the full analysis of the phishing and spam threat landscape over at Securelist. In the meantime, here are a few tips to keep you from becoming a victim. Be sure to share these with your friends and family — especially kids, teens, and older relatives. These groups are often the main targets in the scammers’ crosshairs.
- Check the URL before entering any data. Even if the page looks pixel-perfect, the address bar can give the game away.
- Don’t follow links in suspicious messages, even if they come from someone you know. Their account could easily have been hijacked.
- Never share verification codes with anyone. These codes are the master keys to your digital life.
- Enable two-factor authentication everywhere you can. It adds a crucial extra hurdle for hackers.
- Be skeptical of “too good to be true” offers. Free iPhones, easy money, and gifts from strangers are almost always a trap. For a refresher, check out our post, Phishing 101: what to do if you get a phishing email.
- Install robust protection on all your devices. Kaspersky Premium automatically blocks phishing sites, malicious attachments, and spam blasts before you even have a chance to click. Plus, our Kaspersky for Android app features a three-tier anti-phishing system that can sniff out and neutralize malicious links in any message from any app. Read more about it in our post, A new layer of anti-phishing security in Kaspersky for Android.
 phishing
phishing