The morning of November 24, 2014 is engrained into the collective memories of Sony Pictures Entertainment employees. On that day, an unknown cybergang hacked the company’s server, leaked a slew of confidential data and created a whole lot of reputation repair work for Sony. FBI suspected North Korean hackers. Since then, not much has been known about the culprits. That was until today.
Kaspersky Lab collaborated with Novetta and AlienVault for a joint investigation (dubbed Operation Blockbuster) of the Lazarus group’s activity to benefit the greater good. This gang is believed to be responsible for the Sony Pictures hack and a number of attacks against Seoul-based banks and broadcasters that took place in 2013.
After the notorious Sony Pictures breach our specialists analyzed samples of the Destover malware publicly named as being involved in the attack. The studies revealed traces of dozens cyber campaigns that used different malware samples with a number of common characteristics.
New Version of #Destover #Malware Signed by Stolen @Sony Certificate – http://t.co/mDq0ZRgUgp
— Threatpost (@threatpost) December 9, 2014
Thanks to this investigation Kaspersky Lab was able to proactively spot new malware produced by the same threat actor.
What other things were done by the Lazarus Group did & how did we identify them?
The attackers were actively re-using their developments: they borrowed fragments of a code from one malicious program and implemented it into another. Besides, droppers – the special files used to install different variations of a malicious payload – all kept data within a protected ZIP archive. The password was one and the same in many different campaigns. In fact, it was hardcoded into the dropper.
Even the methods that criminals used to wipe traces of their presence from an infected system were similar which helped to identify the group.
Evidence suggests @Sony hackers are alive & well and still #hacking https://t.co/uEgsLcrOUP #infosec #TheSAS2016 pic.twitter.com/fzcpD7aUOL
— Kaspersky (@kaspersky) February 12, 2016
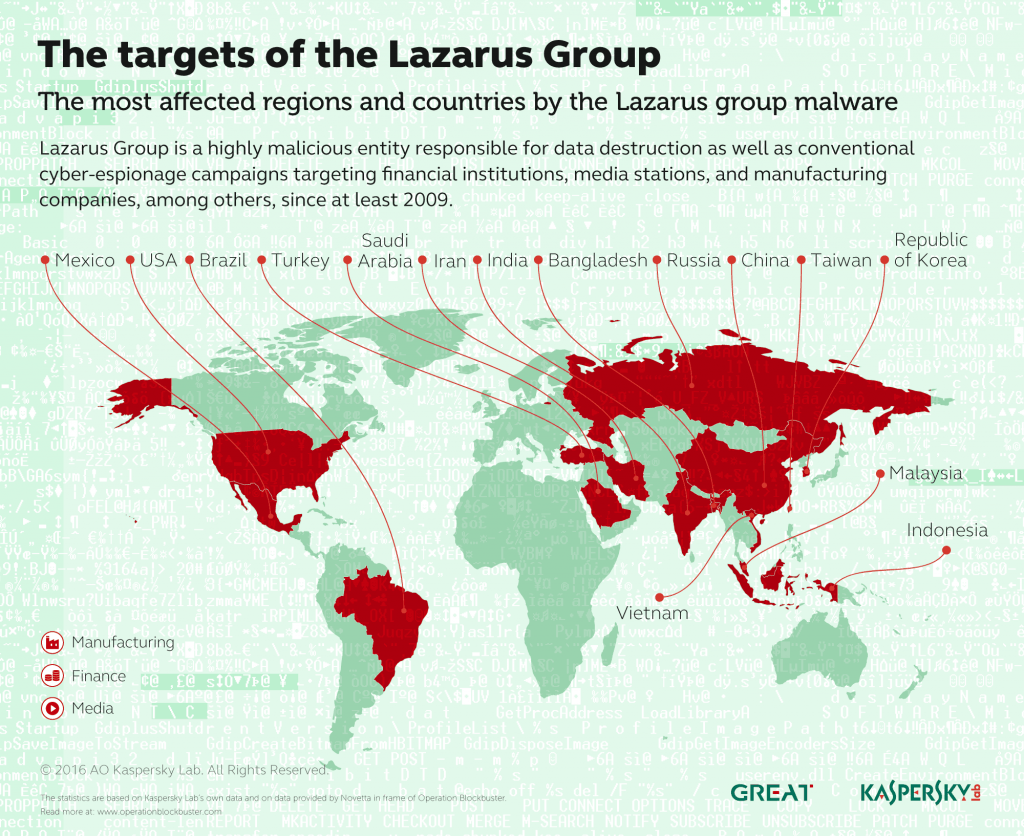
The investigation revealed that Lazarus Group was involved in military espionage campaigns and it sabotaged operations of financial institutions, media stations, and manufacturing companies. As far as we know, most of the victims reside in South Korea, India, China, Brazil, Russia, and Turkey. These criminals created such malware as the Hangman (2014-2015) and Wild Positron (also known as Duuzer, 2015). Wild Positron was a topic of discussion at the Security Analyst Summit 2016.
Kaspersky Lab shared the investigation results with AlienVault Labs. Eventually researchers from the two companies decided to unite their efforts and conduct a joint investigation. It turned out that the activity of the Lazarus Group was also being researched by many other companies and security specialists. One of these companies, Novetta, started an initiative aimed at publishing the results of our investigation as a part of the “Operation Blockbuster,” and we were glad to support it.
Is North Korea Really Behind the Sony Breach?: https://t.co/nb46bzxZXk pic.twitter.com/6nZ4m8Yg0z
— Kaspersky (@kaspersky) December 20, 2014
What do we know about those criminals?
The first malware samples produced by the Lazarus Group date back to 2009. Since 2010 the number of new samples has grown dynamically. This characterizes the Lazarus Group as a stable, longstanding threat actor. In 2014-2015 the group’s productivity was at its highest volume, and the criminals are still active in 2016.
Judging by the activity timetable of the band members, they live in GMT+8 or GMT+9. Criminals start working around midnight (00 hrs GMT) and break for lunch around 3am GMT. Besides, it’s also clear that gang members are extreme workaholics: their working days last 15-16 hours. The Lazarus Group is probably the most hard-working APT-group among all known by us (and we’ve studied a lot of them over the last years).
There is another interesting observation. Judging by the Lazarus group reference sample set, compiled by Novetta, almost two thirds of cybercriminals’ executable files include elements that are typical for Korean-speaking users.
The investigation is still in progress. You can read more about the Lazarus Group and our findings at Securelist.
Operation Blockbuster helped all parties involved find out a lot about this dangerous cybergang. We would not be able to achieve the same results alone due to a number of reasons, including the geographical distribution of security solutions, developed by different companies. Our collaboration gives a great example of how sharing of information helps to identify real criminals and make Internet a safer place.
 APT
APT