The recent price rollercoaster of Bitcoin and other cryptocurrencies have made this topic incredibly hot. Whereas only a year ago cryptocurrencies were the domain of geeks, now all online media are talking about them, and even TV and radio have joined in. Not a day goes by without fresh reports from the cryptomarkets.
But scammers too have been quick to smell the opportunity. Indeed, cryptocurrencies have given phishing — the creation of fake sites to steal credentials from unwary users — a new purpose.
Simple cryptophishing
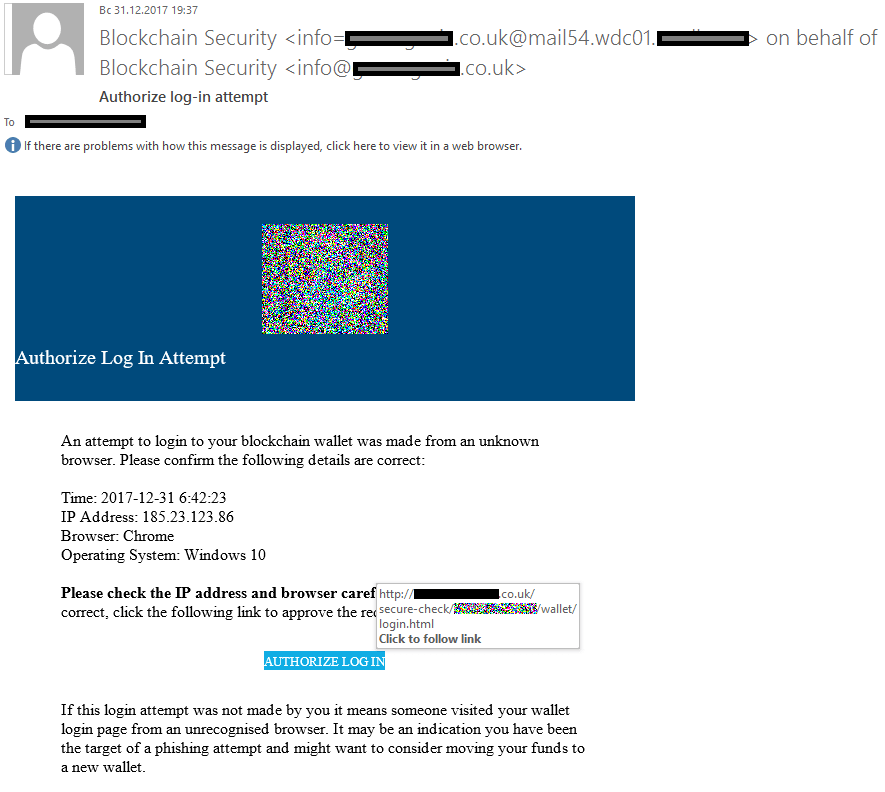
The simplest version of cryptocurrency phishing, aka cryptophishing, involves good old-fashioned spam mailings. In this case, such e-mails appear to originate with providers of cryptocurrency-related services — Web wallets, exchanges, and so on.
The messages are markedly more detailed and sophisticated than the average phishing e-mail. For example, one might be a security alert saying that someone just tried to sign into your account from such and such address using such and such browser — all you have to do is click the link to check that everything’s OK. The potential victim might even have requested such messages on the cryptowallet site, in which case they will notice nothing untoward.
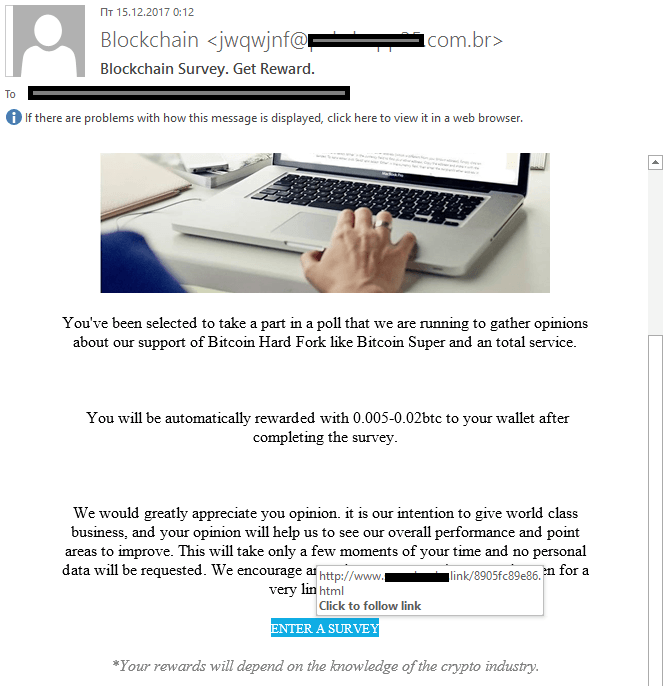
Or it might be an invitation to take a survey about a cryptocurrency event, offering a fairly generous reward for your opinion (say, 0.005 bitcoin, which amounts to about $50–$70 at the current rate). Click on the link, it says, to enter.
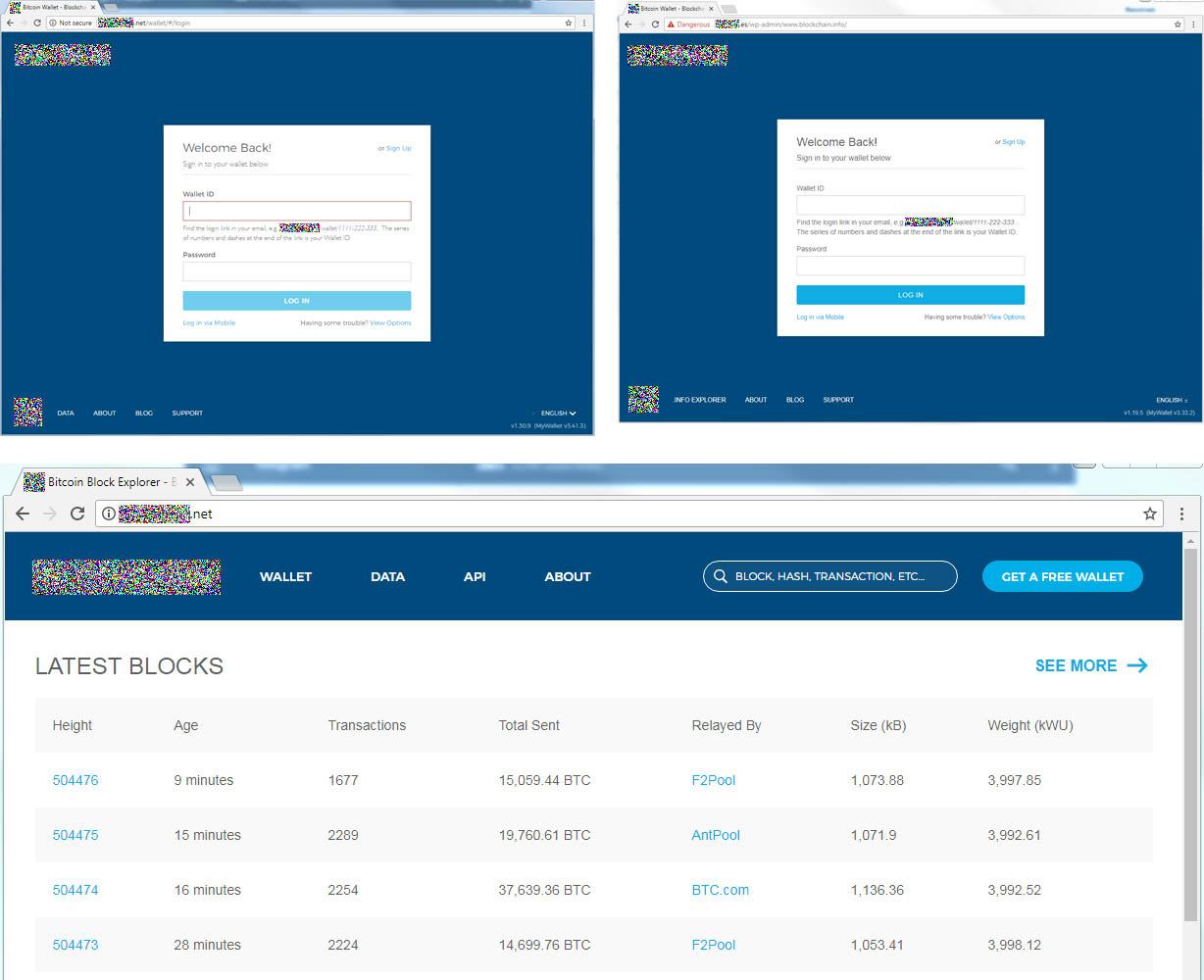
The result is always the same: The victim is directed to a fake version of the expected cryptocurrency site and asked to enter their e-wallet credentials. Most popular Bitcoin Web wallet sites look quite simple, yet recognizable, which helps criminals to create convincing imitations.
The stakes are pretty high: Hijacking an e-wallet that contains a few decibitcoin isn’t like stealing a piffling e-mail account — those fetch some 20 cents per bucket on the black market. In e-wallets, criminals see a quick and direct route to some juicy pickings, so they are investing more in phishing messages and making them more plausible.
Inventive cryptophishing
A more intricate cryptophishing scheme was discovered recently that uses some, shall we say, interesting features of Facebook. Here’s how it works.
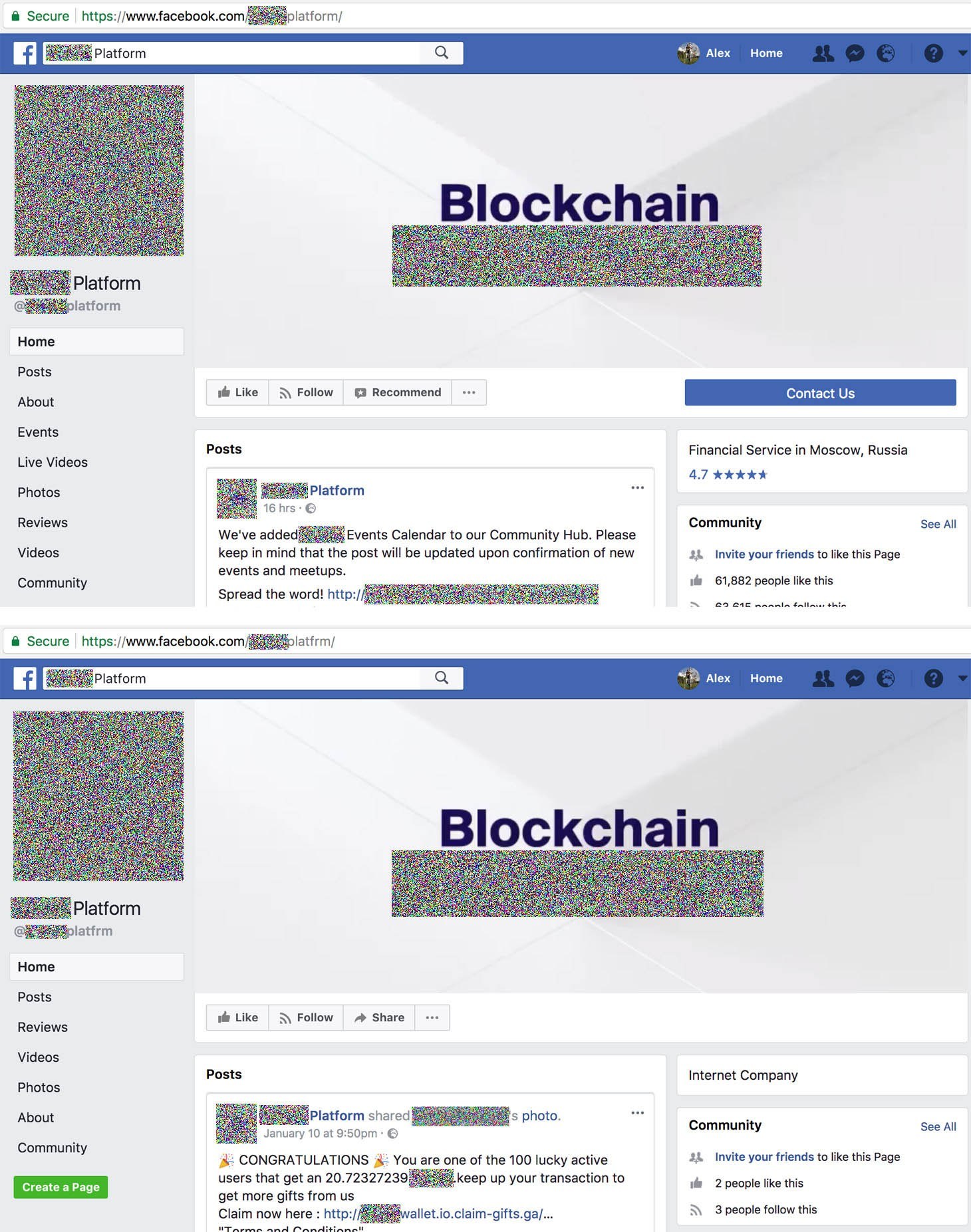
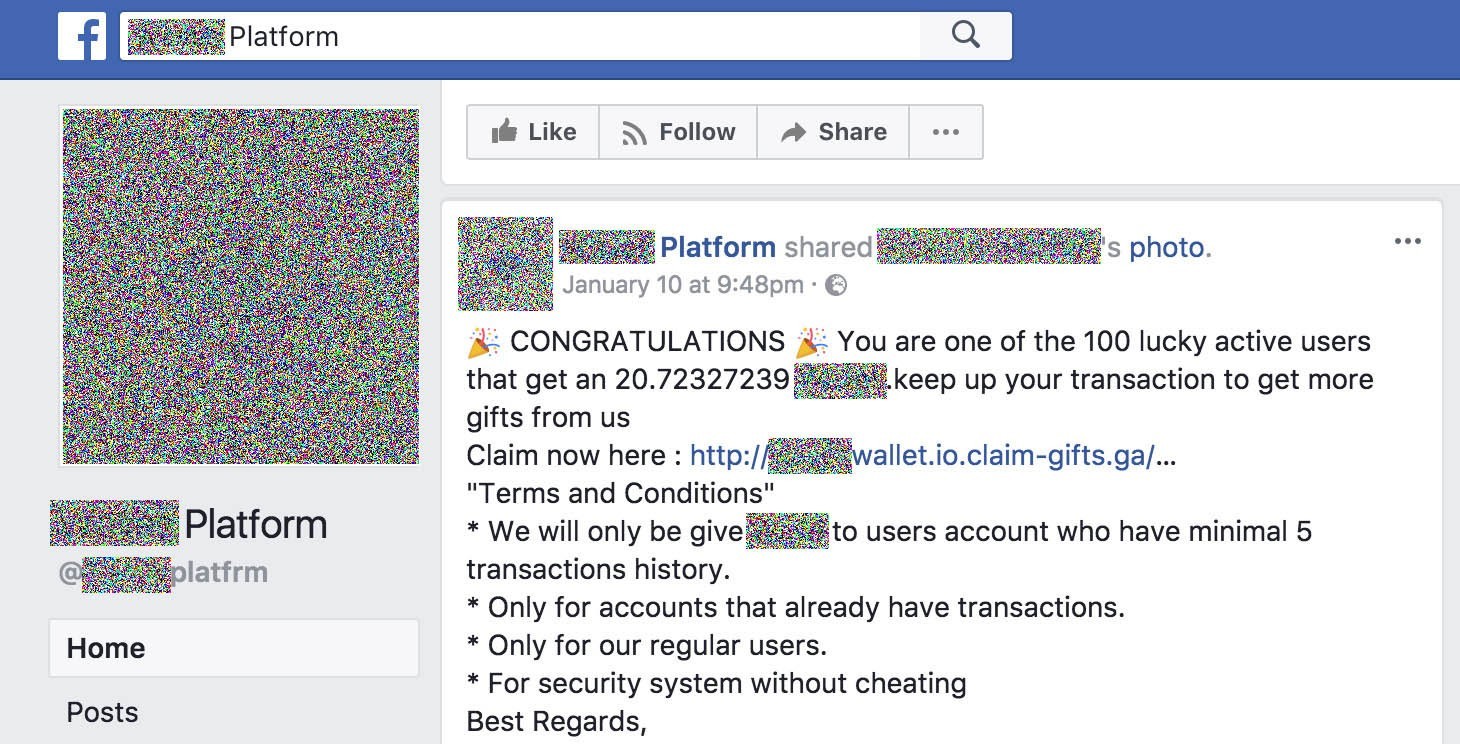
- Scammers find a cryptocurrency community and create a Facebook page with the same title and design as the community’s official page. They make the address of the fake page very similar to that of the real one, differing by as little as one letter. Spotting the difference is not so easy, because in Facebook you can set any name for your organization or yourself, and these names are always displayed far more prominently than real addresses.
- The scammers then send phishing messages to members of the real community from the fake page. Personal messages are not suitable for this purpose for various reasons (for example, they can’t be sent to a user on behalf of a page).So the scammers employ an interesting trick: To target someone, they share the victim’s profile photo on their page and tag them there.The cunning part is that the profile photo is always visible to everyone — and it is not possible to stop someone from sharing it, or tagging you in Facebook — so the trick is effective even against people who are privacy savvy. The only way to stay protected from such activity is to disable notifications about tags created by unknown users, pages, and communities.
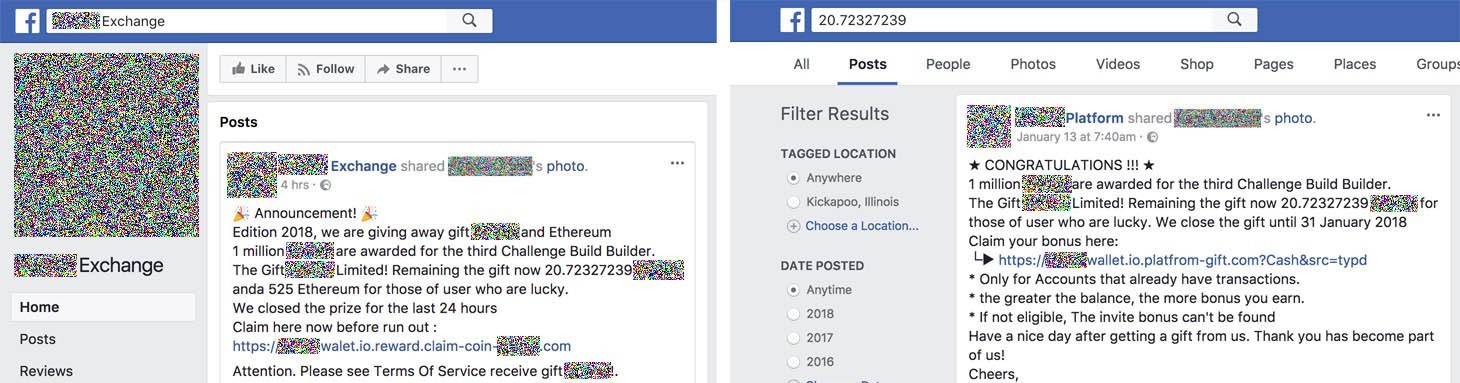
- The most interesting bit is in the text of the message scammers use to mark their prey. For example, the message might say that the user is one of 100 lucky recipients of 20.72327239 (yes, the figure is that precise) cryptocurrency units for their loyalty to the platform. And, of course, there is a link for getting hold of the coins.Note that the message contains detailed terms and conditions for receiving the reward (a minimum number of transactions on the platform, for example). Coupled with the appealingly exact and not excessively high but reasonable amount (about $100–$200), it all seems plausible.
How to guard against cryptophishing
Lately, the cryptomarket may have resembled a magic money tree, but cryptocurrency services are not charities, and they do not give away money for the fun of it. If someone promises you free cryptocurrency, most likely it’s on the end of a hook.
- Always check every link very carefully. It’s best not to click on links in messages from Internet services at all — instead, type in the address of the service in the address bar of your browser.
- Carefully configure your privacy settings to avoid fraudulent schemes in Facebook. See this post for details of how to do that. It’s also not a bad idea to configure Facebook notifications — we have a post about that too.
- Use an antivirus solution with dedicated antiphishing protection. Kaspersky Internet Security is one such solution.
 bitcoin
bitcoin

 Tips
Tips