
VIRUS DEFINITION

Also Called: Trojan-Ransom.Win32.Onion
Virus Type: Ransomware
What is Onion Ransomware?
The “Onion” is an encrypting ransomware which encrypts user data and uses a countdown mechanism to scare victims into paying for decryption in Bitcoins. The cybercriminals claim there is a strict 72-hour deadline to pay up, or all the files will be lost forever. Kaspersky Lab calls the malware the “Onion” because it uses the anonymous network Tor (the Onion Router) to hide its malicious nature and to make it hard to track the actors behind this ongoing malware campaign.
Technical improvements to the malware have made it a potential successor to Cryptolocker, a truly dangerous threat as one of the most sophisticated encryptors today.
How Onion Ransomware Works
To transfer secret data and payment information, the Onion communicates with command and control servers located somewhere inside the anonymous network. Hiding the command server in an anonymous Tor network complicates the search for the cybercriminals, and the use of an unorthodox cryptographic scheme makes file decryption impossible, even if traffic is intercepted between the Trojan and the server. To find out more about the encryption scheme, please see the related blog post on securelist.com
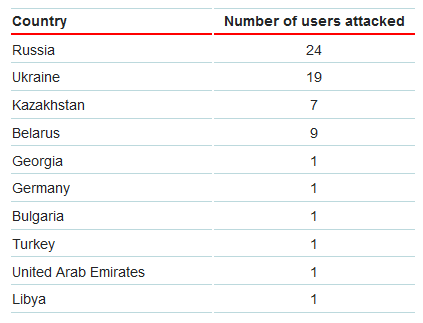
Most attempted infections have been recorded in the CIS, while individual cases have been detected in Germany, Bulgaria, Israel, the UAE and Libya.
Trojan-Ransom.Win32.Onion was detected in the following countries:
For the Onion malware to reach a device, it first goes via the Andromeda botnet (Backdoor.Win32.Androm). The bot then gets a command to download and run another piece of malware from the Joleee family on the infected device. The latter malware then downloads the Onion malware to the device. This is just one of the possible ways that observed of distributing the malware.
How To Protect Yourself
- Back up important files
The best way to ensure the safety of critical data is a consistent backup schedule. Backup should be performed regularly and, moreover, copies need to be created on a storage device that is accessible only during this process (e.g., a removable storage device that disconnects immediately after backup). Failure to follow these recommendations will result in the backed-up files being attacked and encrypted by the ransomware in the same way as the original file versions. - Antivirus software
A security solution should be turned on at all times and all its components should be active. The solution’s databases should also be up to date.





