Over the two years of the pandemic, millions of people learned to use numerous remote collaboration tools. If previously users thought little about security, after the massive uptake of such services, they started paying far more attention to it. Interest in the security of conferencing software has yet to abate, in which regard researchers at three U.S. universities published a study on whether the microphone mute button in popular tools actually does what it says on the tin. The results were varied, yet undoubtedly suggest that it’s time to reconsider attitudes to privacy during work calls.
Where did the idea come from?
Actually, the idea was quite obvious. If you’ve ever used Microsoft Teams, you’ll surely be familiar with the following situation: you connect to a call in Mute mode, forget to turn it off and start talking, whereupon the program reminds you that the microphone is muted. Clearly, such an (admittedly handy) feature cannot work if the mute button disconnects the microphone altogether. How, then, is this feature actually implemented? And is sound from the microphone sent to the solution vendor’s server even in Mute mode?
These are some of the questions posed by the authors of the study. But how to check? For this, the researchers analyzed the intricacies of microphone interaction for ten services, in each case examining the scenario for browser-based calls.
Research results
From a privacy point of view, the best solution for conference calls would appear to be a web client. All web-based conferencing services were tested in a browser based on the Chromium open-source engine (the basis of many browsers, including Google Chrome and Microsoft Edge). In this mode, all services must comply with the rules for microphone interaction, as set by the developers of the browser engine. That is, when the microphone mute button is activated in the web interface, the service should pick up no sound at all. Native desktop applications have more rights.
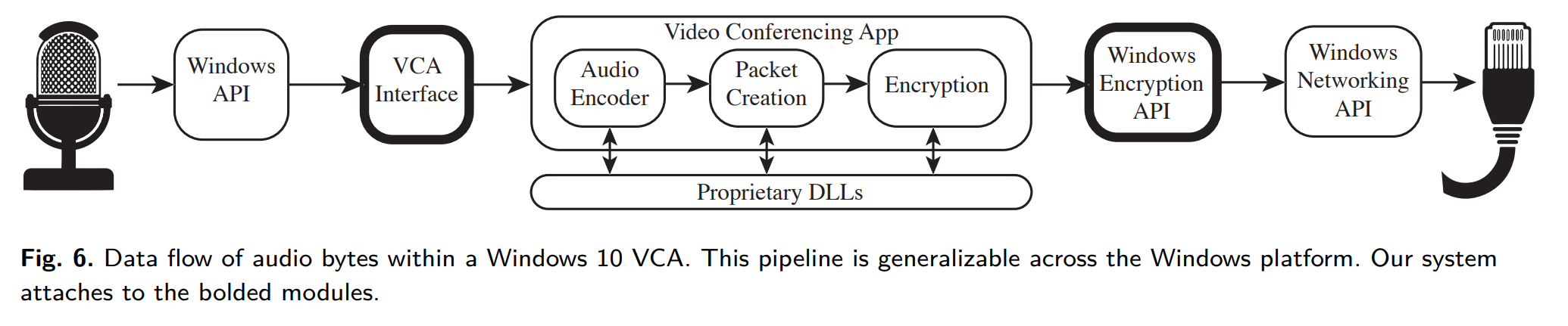
General scheme of interaction between native conferencing application and operating system (in this case Windows 10). Source
The researchers analyzed how and when the application interacts with the microphone by comparing audio data captured from the microphone with the stream of information sent to the server. And they found that different programs have different behavior. Here’s what they learned about the most popular services.
Zoom
The Zoom client provides an example of “decent” behavior. In Mute mode, it does not capture the audio stream; that is, it does not eavesdrop on what’s going on around you. That said, the client regularly requests information that allows it to determine the noise level near the microphone. As soon as the silence ends (you start talking or just make a noise), the client reminds you, as ever, to turn off Mute mode.
Microsoft Teams
Regarding the above-mentioned native client for Microsoft Teams, things are slightly more complicated: the program doesn’t use the standard system interface for microphone interaction, and instead communicates directly with Windows. As such, the researchers were unable to investigate in detail how the Teams client handles muting during a call.
Cisco Webex
The Cisco Webex client displayed the most unusual behavior. Unique among all the solutions tested, it constantly processed the sound from the microphone during the call, regardless of the state of the Mute button inside the application. However, investigating the client in more detail, the researchers found that Webex does not snoop on you: in Mute mode, sound is not transmitted to the remote server. But it does send metadata; specifically — the volume level of the signal.
On the face of it, this doesn’t seem like a big deal. However, solely on the basis of this metadata, without access to the actual audio stream, the researchers were still able to determine a number of basic parameters of what was happening at the user’s end. For example, it was possible to determine with a reasonable degree of reliability that the user had turned off the microphone and camera, and turned on his vacuum cleaner. Or cooking. Or that a dog was barking. It was possible to know if others were present in the room (for example, that the call was coming from a public place). This involved the use of an algorithm similar in some ways to that of Shazam and other music discovery apps. For each “noise sample”, a set of patterns is created and compared to the data captured from the Cisco Webex client.
Privacy levels
The study offers some practical advice and confirms one obvious fact: you don’t have full control over what data is collected on you or how. A positive takeaway from the report is that it found no crime in the operation of popular conferencing tools. Many applications tread very carefully when it comes to microphone use.
If, despite these positive results, you’re still uneasy about having a native application on your computer with constant access to the microphone, a simple solution, if possible, is to connect through a web client. Sure, the functionality will be limited, but privacy will increase: the Mute button there really does disconnect the microphone from the service.
Another option is a hardware microphone Mute button, if there is one on your computer. Or an external headset — the Mute button on top-of-the-range models often isolates the microphone from the computer physically, not by software means.
The real danger is not the conferencing tools themselves, but malware that can snoop on victims and send audio recordings of important conversations to its creators. In this case, you need not only a security solution that deals with unwanted programs, but also a means of controlling who accesses the microphone and when — in case a legitimate program decides to do so without asking. Kaspersky’s solutions for both home and business feature a separate function that informs you when software tries to access the microphone or webcam.
 privacy
privacy
