The ransomware group Interlock has started using the ClickFix technique to gain access to its victims’ infrastructure. In a recent post, we discussed the general concept of ClickFix. Today we’ll look at a specific case where a ransomware group has put this tactic into action. Cybersecurity researchers have discovered that Interlock is using a fake CAPTCHA imitating a Cloudflare-protected site on a page posing as the website of Advanced IP Scanner — a popular free network scanning tool. This suggests the attack is aimed at IT professionals working in organizations of potential interest to the group.
How Interlock is using ClickFix to spread malware
The Interlock attackers lure victims to a webpage with an URL mimicking that of the official Advanced IP Scanner site. The researchers found multiple instances of this same page hosted at different addresses across the web.
When the user clicks the link, they see a message asking them to complete a CAPTCHA, seemingly provided by Cloudflare. The message states that Cloudflare helps companies “regain control of their technology”. This legitimate-looking marketing text is in fact copied from Cloudflare’s own What is Cloudflare? webpage. It’s followed by instructions to press Win + R, then Ctrl + V, and finally Enter. Next come two buttons: Fix it and Retry.
Finally, a message claims that the resource the victim is trying to access needs to verify the connection’s security.
In reality, when the victim clicks Fix it, a malicious PowerShell command is copied to the clipboard. The user then unknowingly opens the command console with Win + R and pastes the command with Ctrl + V. Pressing Enter then executes the malicious command.
Executing the command downloads and launches a 36-megabyte fake PyInstaller installer file. And to distract the victim, a browser window with the real Advanced IP Scanner website opens.
From data collection to extortion: the stages of an Interlock attack
Once the fake installer is launched, a PowerShell script is activated that collects system information and sends it to a C2 server. In response, the server can either send the ooff command to terminate the script, or deliver additional malware. In this case the attackers used Interlock RAT (remote access Trojan) as the payload. The malware is saved in the %AppData% folder and runs automatically, allowing the attackers to access confidential data and establish persistence in the system.
After initial access, the Interlock operators try to use previously stolen or leaked credentials and the Remote Desktop Protocol (RDP) for lateral movement. Their primary target is the domain controller (DC) — gaining access to it allows the attackers to spread malware across the infrastructure.
The final step before launching the ransomware is to steal the victim organization’s valuable data. These files are uploaded to Azure Blob Storage controlled by the attackers. After exfiltrating the sensitive data, the Interlock group publishes it on a new Tor domain. A link to this domain is then provided in a new post on the group’s .onion site.
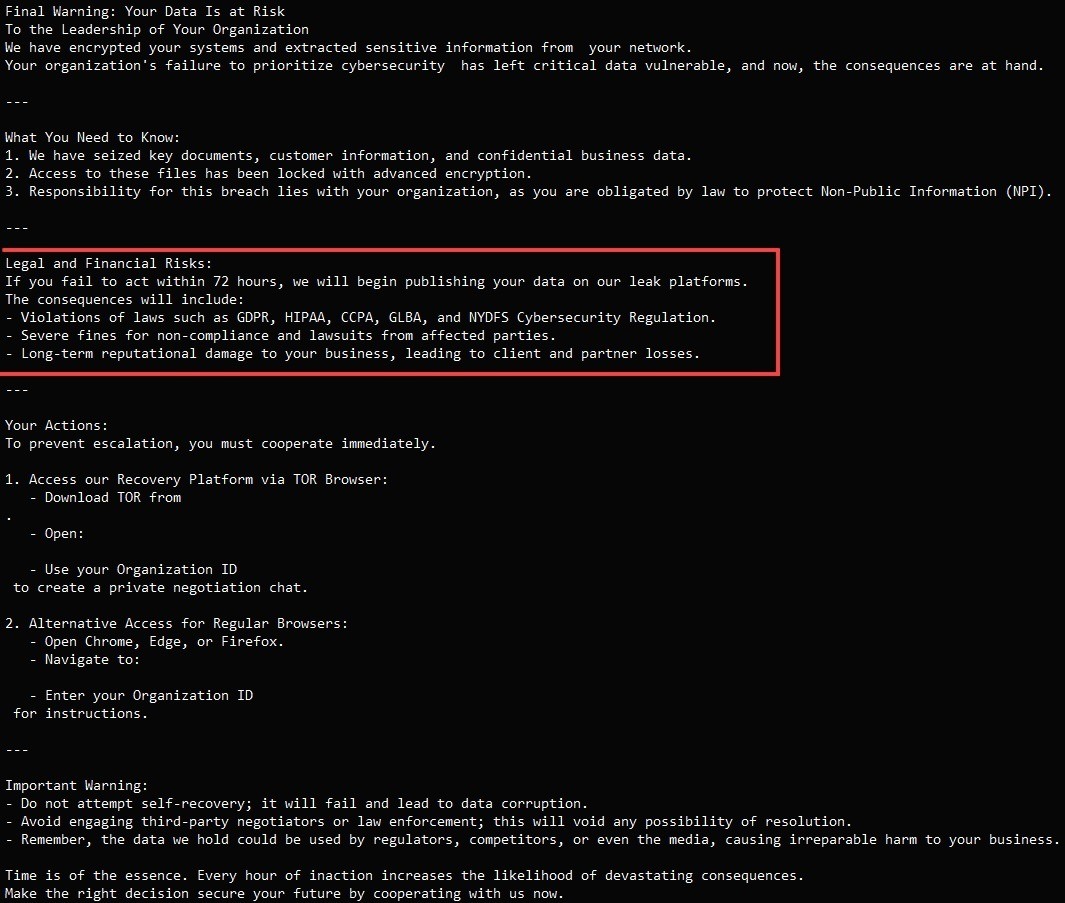
Example of a ransom note sent by the Interlock ransomware group. Source
How to protect against ClickFix attacks
ClickFix and other similar techniques rely heavily on social engineering, so the best protection is a systematic approach focused primarily on raising employee awareness. To help with this, we recommend our Kaspersky Automated Security Awareness Platform, which automates training programs for staff.
In addition, to protect against ransomware attacks, we recommend the following:
- Installing reliable protection on all corporate devices.
- Monitoring for suspicious activity in the corporate network using an XDR-class solution.
- If your in-house security team lacks the resources or expertise, using an external service for threat hunting and response.
 ransomware
ransomware
